
Am I Paranoid About Online Security?
I normally don’t have much trouble choosing a New Year’s Resolution, but this year has been tough. I just couldn’t think of something really important that I wanted to commit to. Well, a few days ago,...

I normally don’t have much trouble choosing a New Year’s Resolution, but this year has been tough. I just couldn’t think of something really important that I wanted to commit to. Well, a few days ago,...
Learn how to enable or disable the dark theme in Remote Desktop Manager. Follow our simple steps to switch between themes and customize your user interface for a better experience.

As an IT pro, you probably read the equivalent of a book a month – or maybe even a book a week. All of those emails, memos, articles, white papers, reports…and let’s not forget the endless TPS reports...


Organizations rely on privileged accounts to drive productivity and efficiency. Unfortunately, hackers also rely on vulnerable privileged accounts to breach networks, access critical systems, and stea...

Celebrate the holiday season with Devolutions! Read our special 2019 holiday message, filled with appreciation and joy. Thank you for your support and loyalty throughout the year.

Learn how to prevent file upload vulnerabilities with our essential security practices. Protect your system from malicious uploads by following these best practices and advanced protection techniques.

As you may be aware, some companies such as Apple have decided to retire (a.k.a. deprecate) support for the 32-bit version of their applications. We have been thinking of making the same change to Rem...

Over the last few years, SMBs have become ground zero for cybercrime. To combat this threat, we invite you to click on the link below for a new white paper from international and independent analyst o...
In a recent article on cybersecurity tips that parents should teach their kids, we highlighted how, contrary to what many people believe, home wireless networks can be highly insecure. Unfortunately, ...
The Black Friday deals are over and 2019 is coming to an end, but we still have something in store to satisfy the Rust developers among you. Today, we are announcing MongoDB CWAL, a community-supporte...

December is here, which means that in a little while we’ll be spending time with family and friends, eating and drinking great stuff (and then wishing we didn’t eat and drink so much!), and of course,...

Recently, we introduced you to Devolutions Password Hub (DPH), our new cloud-based password management solution for teams, which features: ,Robust Enterprise Grade Security ,Cloud-Based for Scalabil...

The following is a guest blog written by highly experienced IT pro Francois Fournier. Francois was one of the very first RDM users, and he has been a valued and important part of our community for mor...
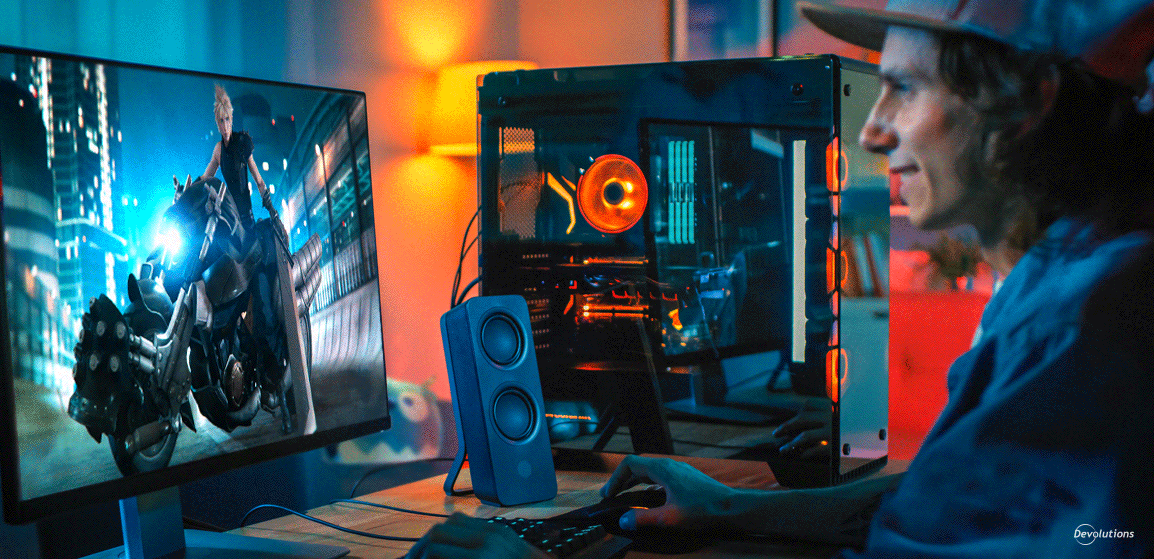
Hello fellow gamers! Video games have come a LONG way since 1962, when researchers at MIT launched the very first computer-based video game called Space Wars. To celebrate World Video Game Day on Nove...

Learn how to register Remote Desktop Manager Free with our quick and easy guide. Follow these simple steps to set up and start using RDM Free for efficient remote access management.

Amazon Web Services (AWS) provides a cloud platform for information storage and data processing to millions of clients around the world, including militaries and governments. It’s one of the most powe...

We are pleased to share that Devolutions’ PAM solution is featured in a new report by KuppingerCole Analysts. KuppingerCole Analysts is an international and independent analyst organization headquarte...

The first Sysadminotaur animated short is finally here and we can't contain our excitement! Watch it now! To learn more about the making of, read the interview we had with the Sysadminotaur creator, P...