Over the last few weeks, we’ve been focusing on RDM’s role based security system and exploring the difference between roles and permissions set on entries. Today, we’ll look at a new feature: implementing the same level of security to your data sources.
For those users with experience with RDM, it’s the natural evolution of what we used to call privileges and/or rights. By leveraging our new role based security system we’ve made the management of such permissions much better.
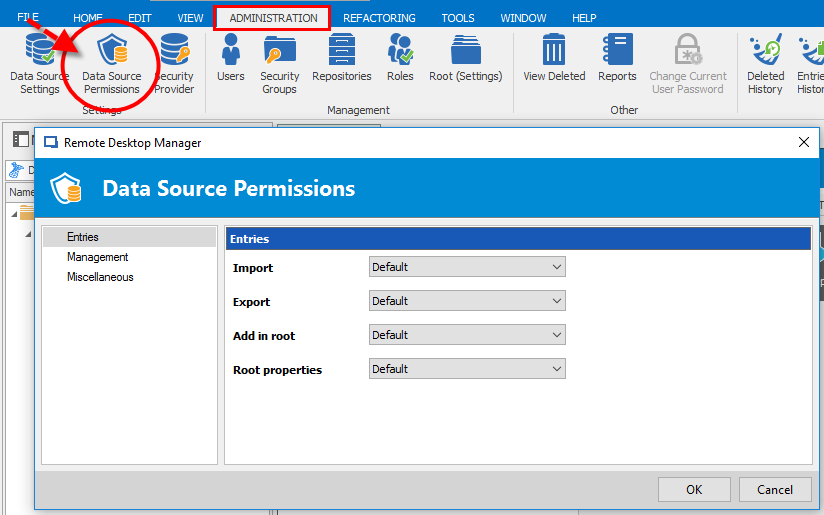
Simply open the Administration menu, and you’ll see a new feature called Data Source Permissions. Once you click it, you’ll be able to manage three permissions’ categories: Entries, Management and Miscellaneous.
Let’s take a closer look at each of these categories:
Entries
This section lets you assign permissions to users or roles on the entries that are held in the data source. For example, you can determine if a user can import or export from the data source, and manage whether a user can add anything to the root or edit the root properties. Keep in mind that if export rights are given, a user will be able to view the username/password linked to an exported entry.
Management
This section lets you assign data source management permissions to users or roles. This control is usually given to the data source administrator, since it covers all users, roles, repositories, and provides the ability to modify data source settings.
Miscellaneous
This section lets you assign various data source permissions to users and roles. For example, you can enable a user to view usage logs, reports, and see what has been deleted from the data source.
A Word of Caution
As you might expect, we strongly urge you to be cautious when handing out these permissions, as the wrong access in the wrong hands could be disastrous. Think of your data source like a safe – permissions are the combination to open it.
As always, please let us know your thoughts by using the comment feature of the blog. You can also visit our forums to get help and submit feature requests, you can find them here.




