Devolutions Server is a self-hosted management solution that enables your organization to secure, control, and monitor access to privileged accounts and business user passwords. In addition, Devolutions Server seamlessly integrates with our remote connection and management solution Remote Desktop Manager. Once combined, Devolutions Server plus Remote Desktop Manager establishes a powerful all-in-one privileged account and session management platform that supports over 150 tools and technologies.
In this article, we look closer at how to share credentials or assets with guests who are outside your organization. If you have already configured single sign-on with your Azure AD tenant, then you can leverage the built-in guest management functionality from Azure AD directly in Devolutions Server. The setup process is fairly easy and provides several advantages including:
- Centralized control over guest-user 2FA (per Azure)
- Centralized control over the guest-user access (per Azure)
- Visibility of authentication logs (per Azure)
- The ability to let guest users maintain their existing ID, which makes onboarding faster and easier (per Azure AD)
- The ability to control identity lifecycle management from your identity provider. When you revoke guest access to your tenant, they no longer have access to Devolutions Server.
- The ability to securely share data with individuals outside the organization (per Devolutions Server)
A Word of Caution
Please note that Devolutions Server does not automatically make the distinction between a guest user and a normal user. If Azure AD users (who we can assume are full-fledged members of the organization) are granted a wide range of privileged access by default, then it is possible that a guest user may be given too much power.
We strongly recommend that you verify that access is appropriate for guest users who connect with Azure AD. If it isn’t, then you’ll want to make the necessary changes.
Workflow for Admins
Here is the workflow for Admins who want to invite a guest user:
Step 1: Invite the guest user via the Azure AD (now Entra ID) tenant.
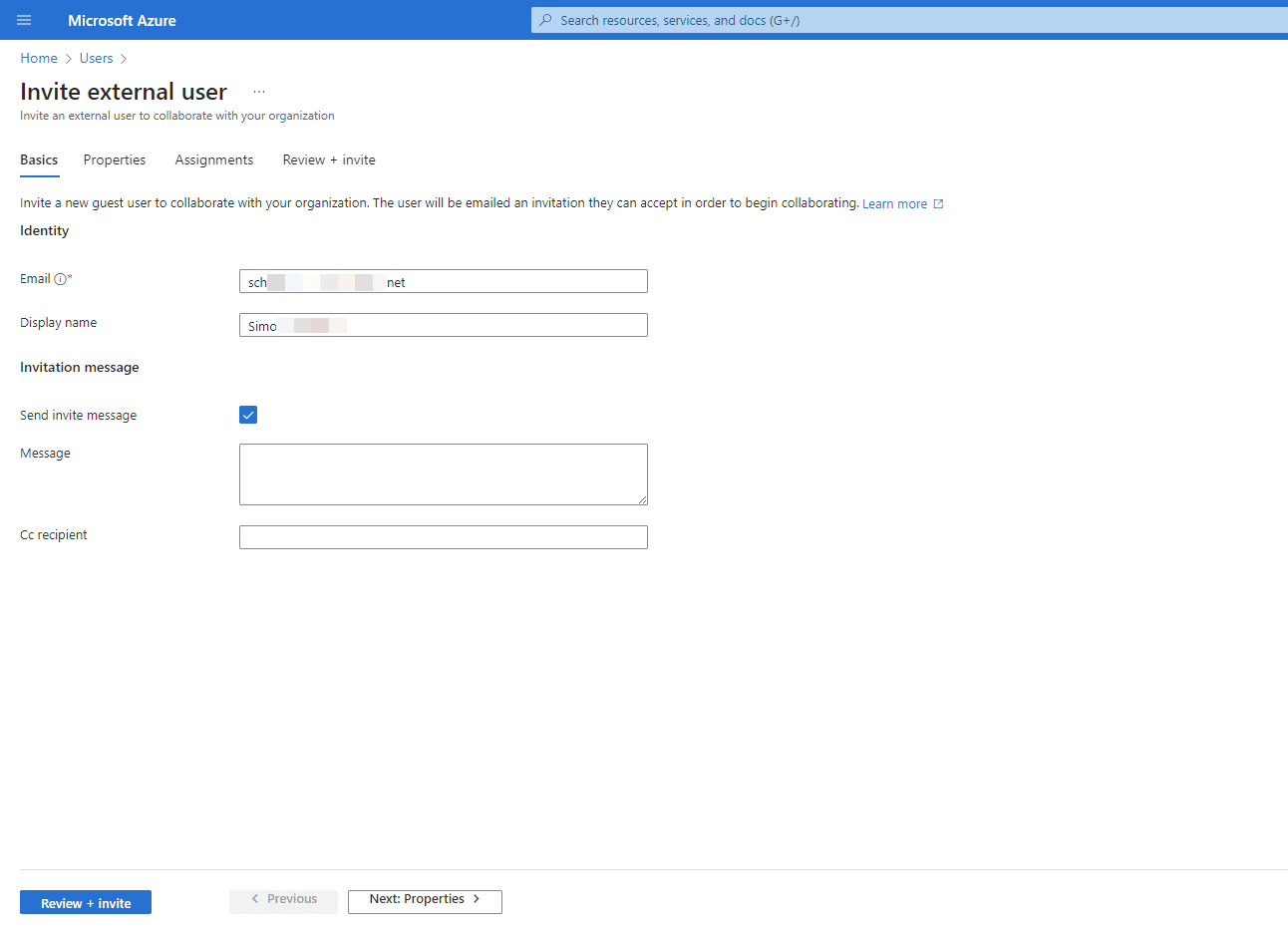
Step 2: Note the generated username (user_domain#EXT#@org.onmicrosoft.com) for the guest user. This will be required to add them to Devolutions Server (see next step).
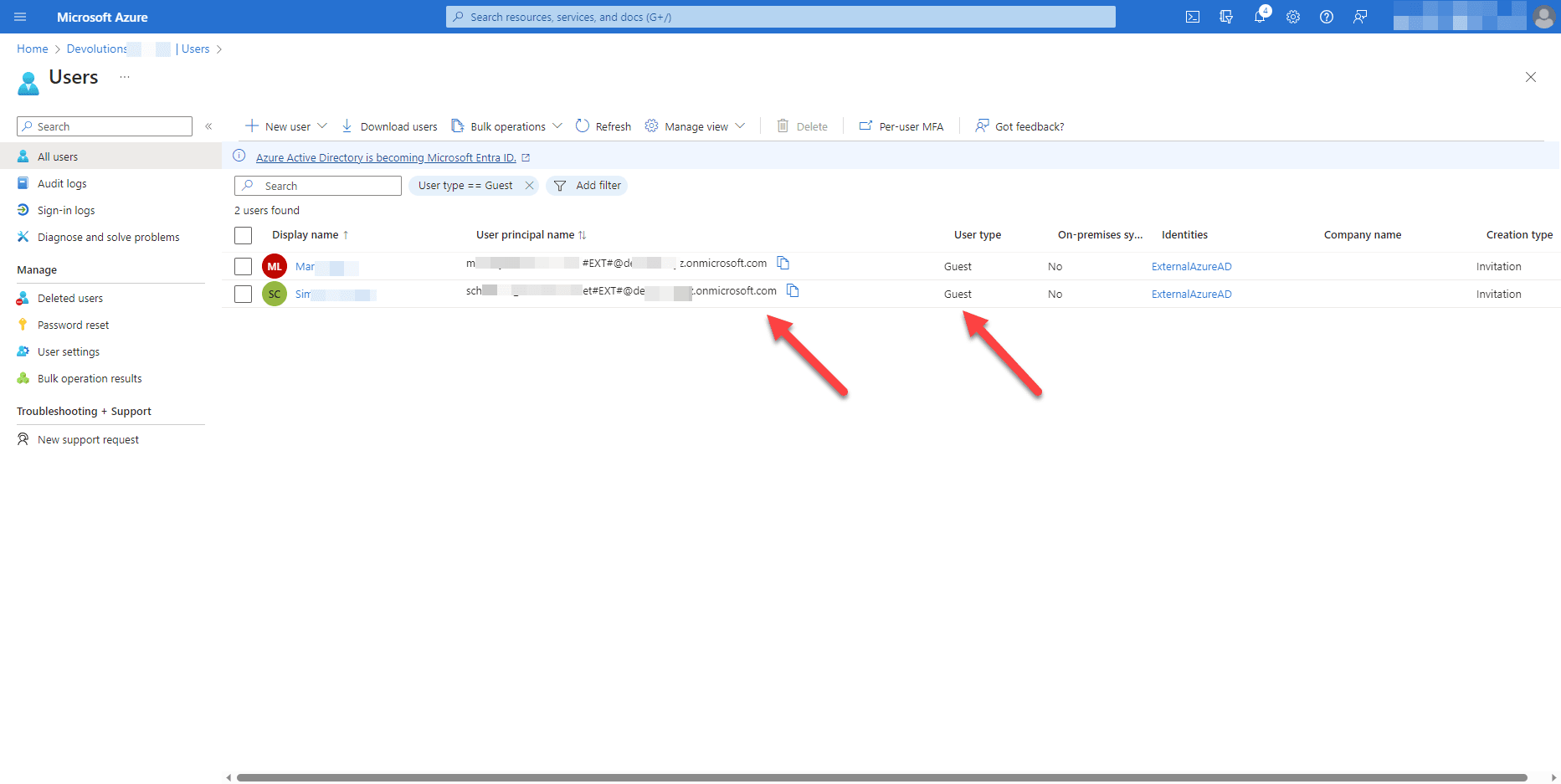
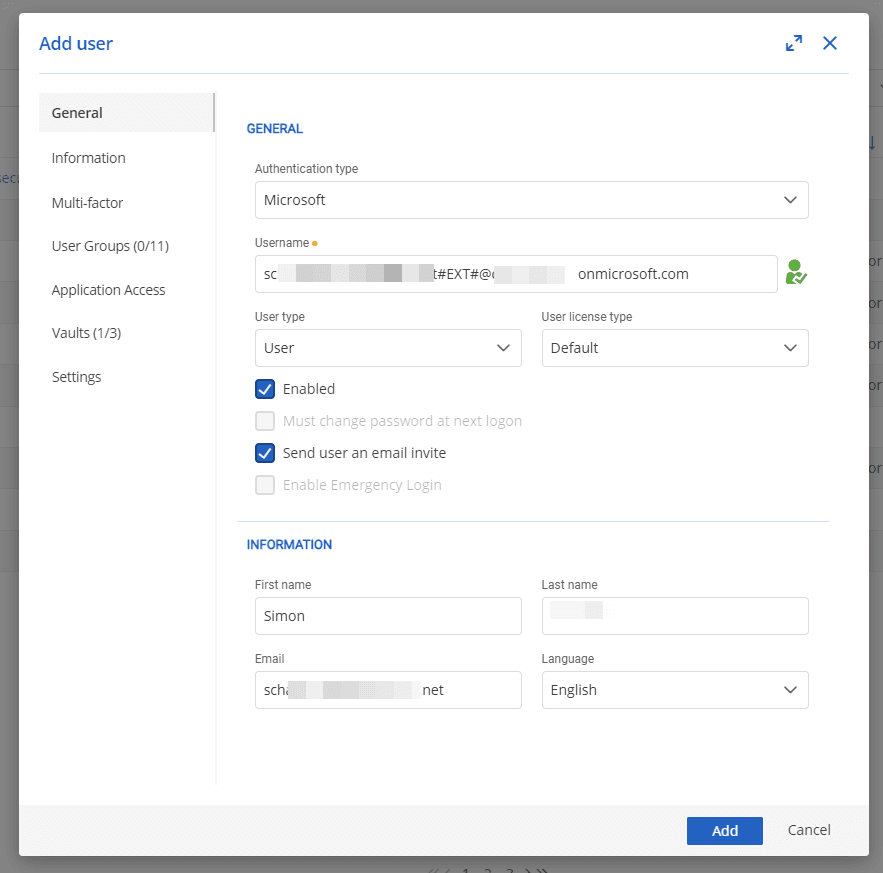
Step 3: Invite the guest user to Devolutions Server with the username that was generated in the previous step. Choose the access level: standard, restricted, or read-only. For obvious reasons, we do not recommend giving a guest user Administrator access!
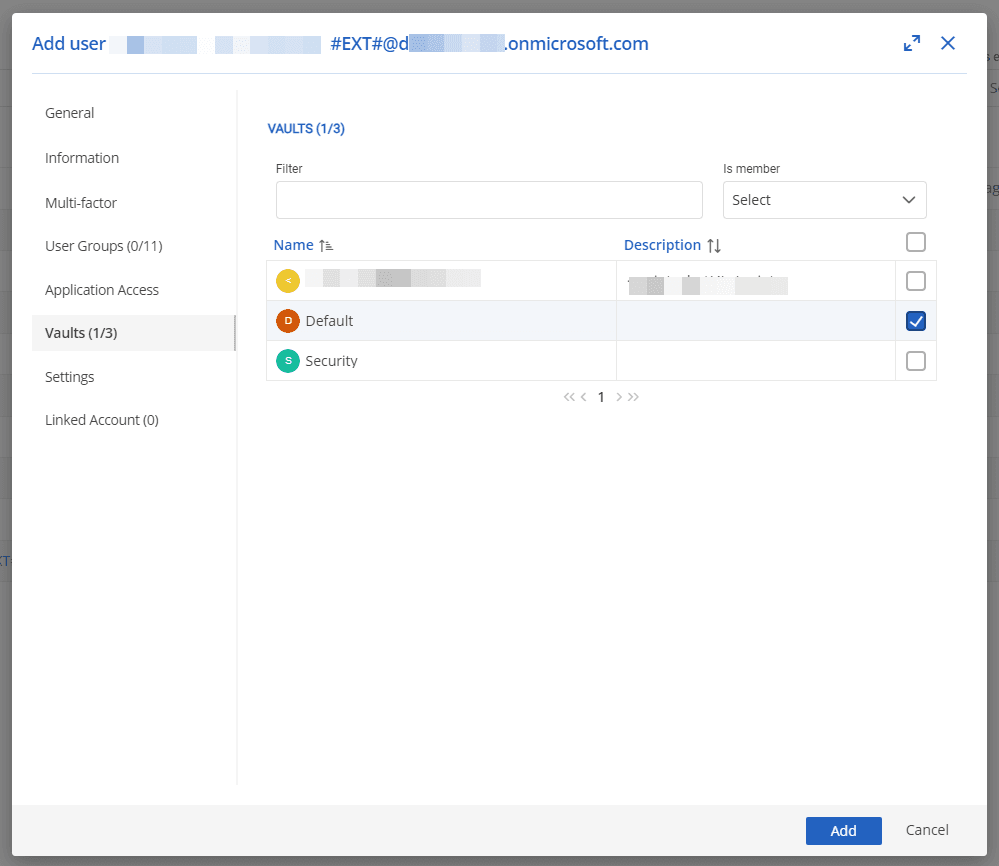
Step 4 (Optional): Select the vaults and settings for the guest user (this can be done at a later time if desired).
Additional Considerations
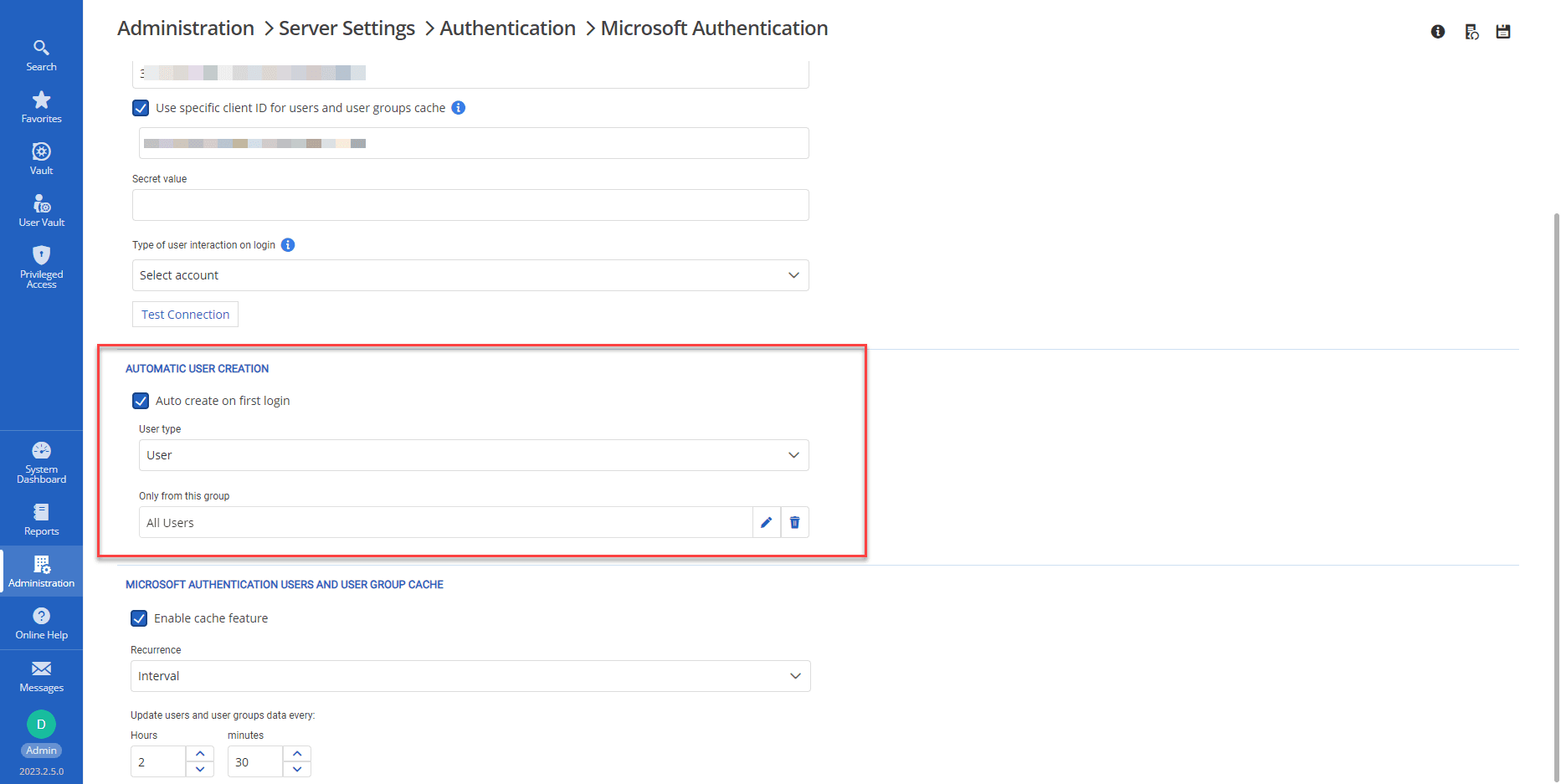
Automatic Guest User Creation (and Override Option)
If Devolutions Server is configured to automatically create a new user on first login, then the guest user does not need to be manually added. However, the guest user must be a member of the Azure AD group that is permitted to access Devolutions Server (if such a group is specified in the configuration).
In this use case, the guest user will inherit all default permissions. As such, it is essential to verify that this access is appropriate for the organization.
Also, even with this configuration, an Admin can still proactively create a guest user account and set the permissions before that user logs in for the first time.
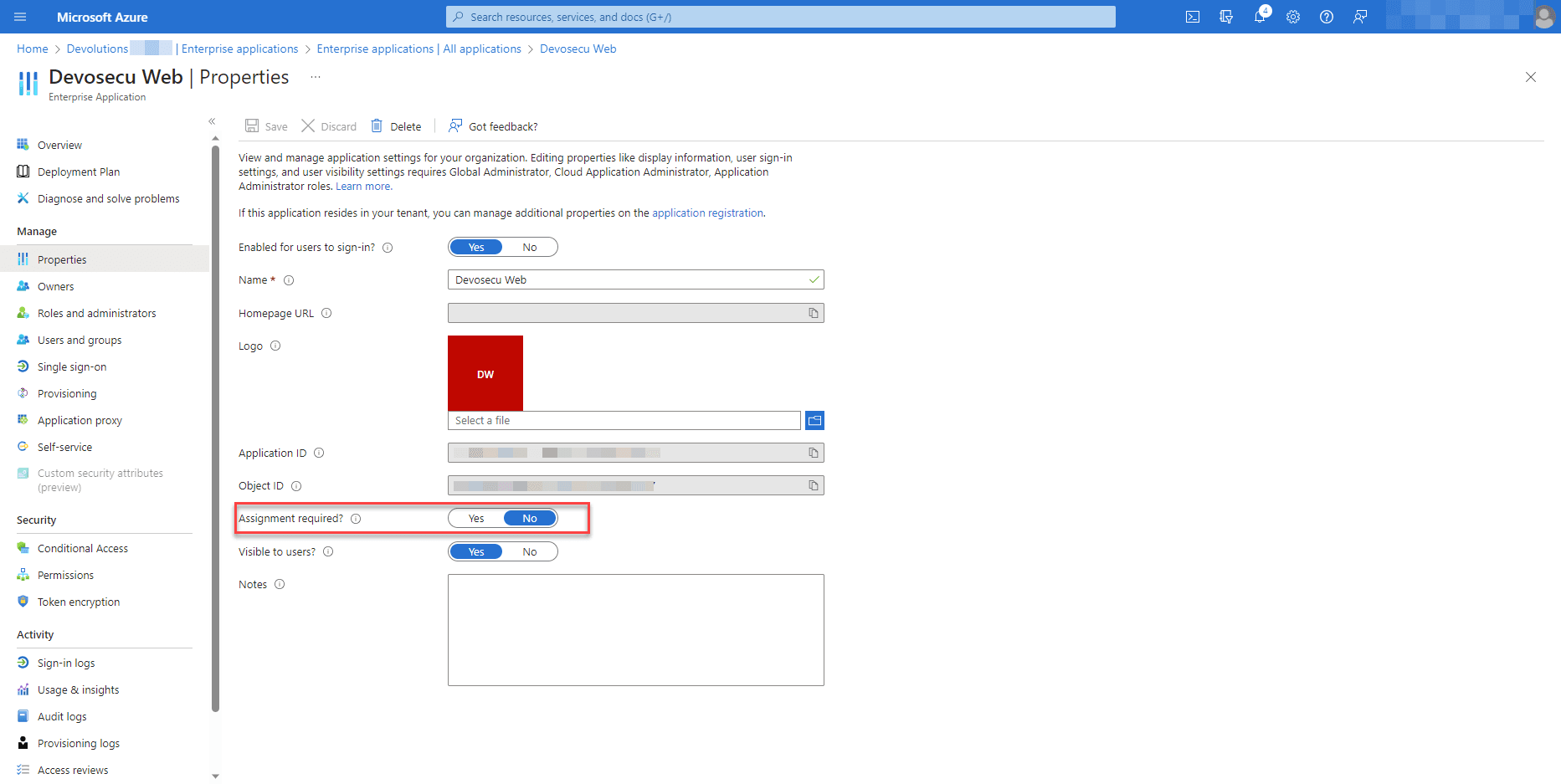
Assignment
If the Azure AD Enterprise Application for the Devolutions Server login is configured to require assignment of users (Assignment Required set to “Yes”), then the guest user must be assigned to the application, or must be a member a group assigned to the application.
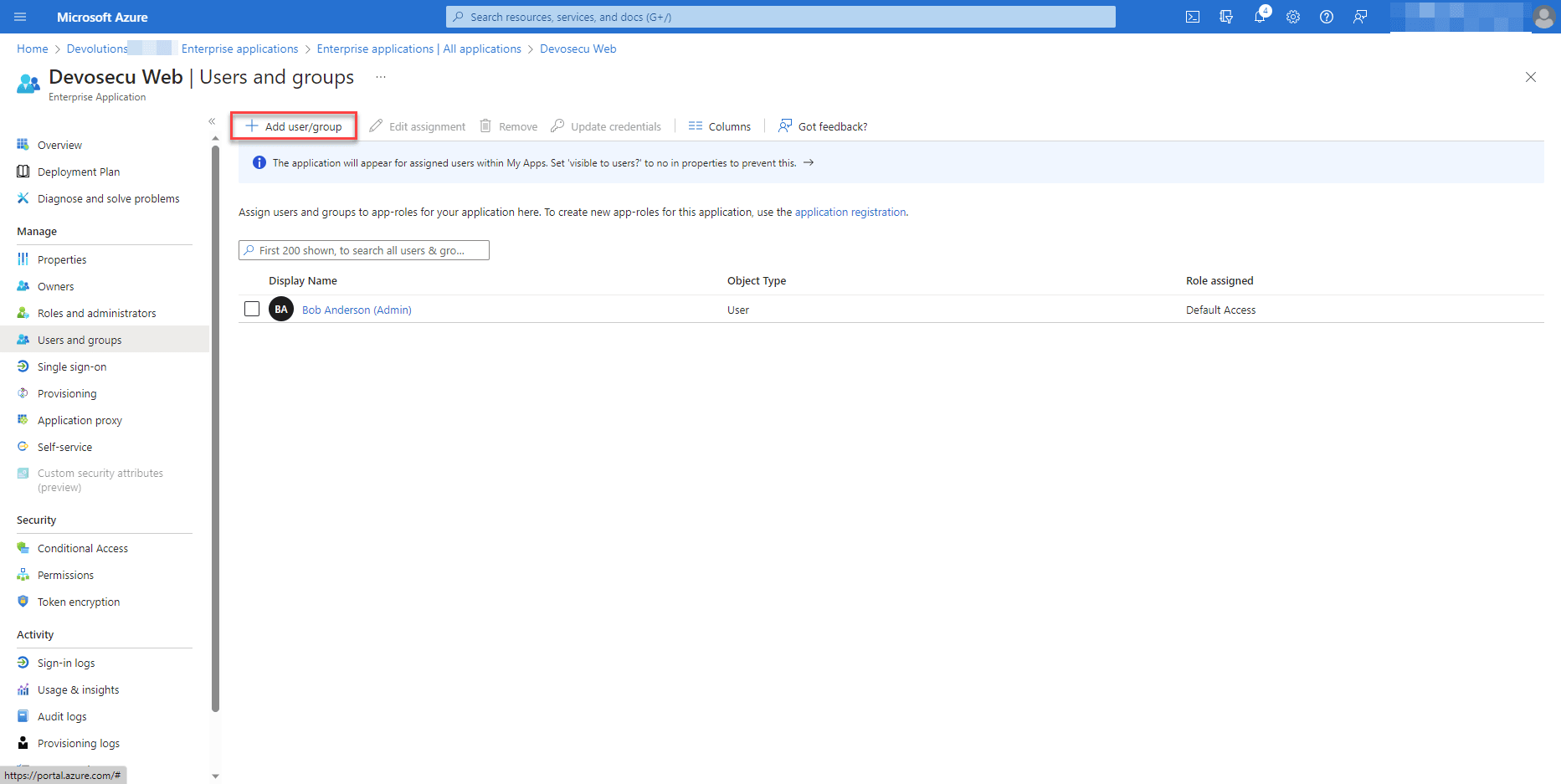
User Experience for Guests
Here is how things look from the guest user’s perspective:
The guest user receives an email invitation:
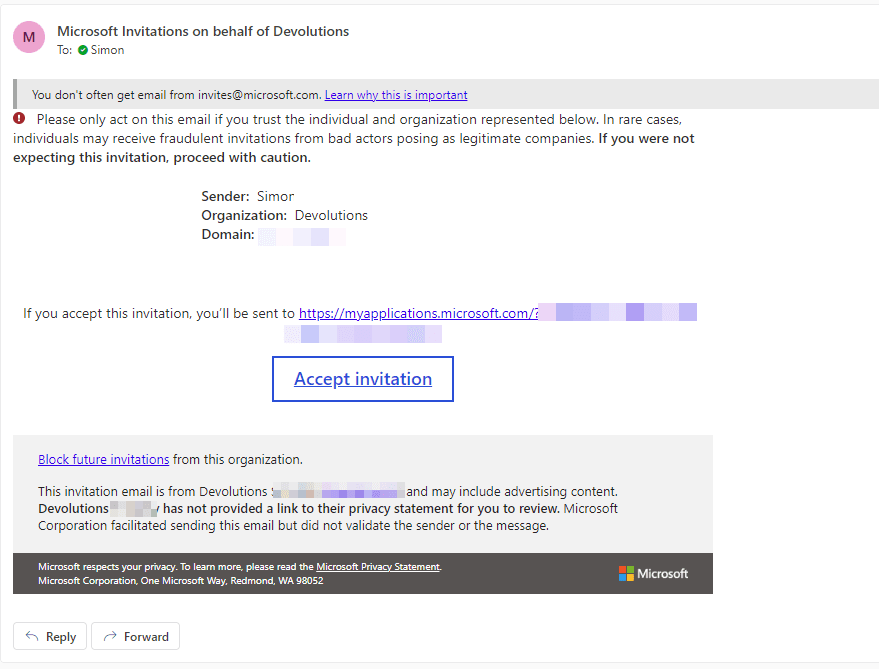
Once the guest user accepts the email invitation, they are prompted to grant permission to transmit required information (e.g., profile data, activity log, etc.):
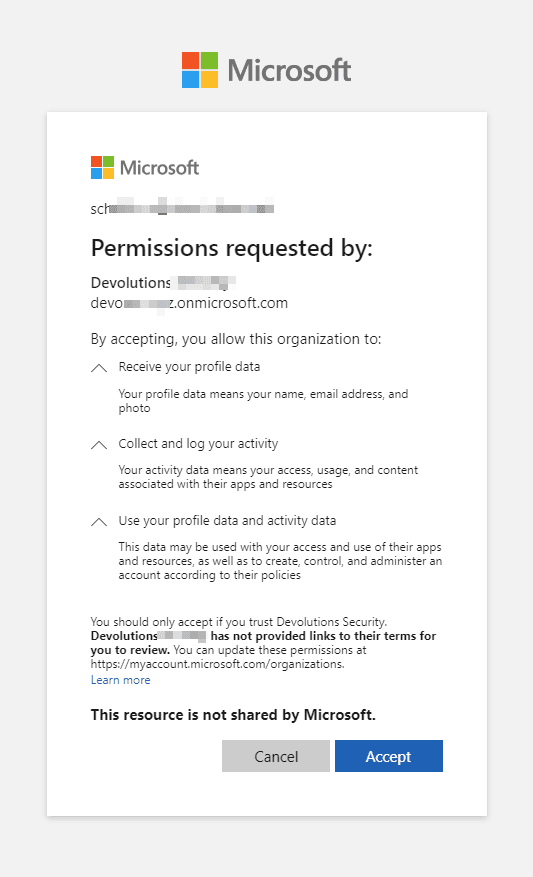
Once the guest user accepts the request, they are prompted to choose their authentication method. Note: The guest user must select Microsoft as the authentication method, and not Devolutions Server.

Finally, the guest user signs in to Devolutions Server, passes the MFA challenge (code sent via email or text), and can access the resources according to their permissions:
Questions? We Can Help!
If you have any questions about guest access in Devolutions Server, then our Support Team is happy to help.
We also invite you to let us know what you think about this (and any other) feature. We rely on your feedback to make ongoing improvements. Please comment below, post in our forum, or get in touch with us directly. We are always listening to you!
Dive Deeper into Devolutions Server
Interested in learning more about Devolutions Server? Here are some suggestions:
- An overview of some of the major improvements and additions in the latest version of Devolutions Server – read now
- An overview of the benefits of integrating Devolutions Server with Remote Desktop Manager (along with other paired solutions) – read now
- A closer look at Devolutions Gateway, which is designed to work with Devolutions Server and provides authorized just-in-time access to resources in segmented networks – read now
- An overview of Devolutions Server subscription options & additional tools/modules – read now
- Securing the Slack primary owner in Devolutions Server PAM – read now





