Modern organizations rely on messaging tools for both internal and external communications. Slack is no exception and has become more important with the widespread adoption of remote work. To set up a new Slack organization, a Primary Owner account must be created, containing unfettered access and privilege, similar to the "root" account in Linux.
Messaging tools, like Slack, contain critical business information beyond water-cooler chatter. No organization would want a threat actor to gain access to such details. This raises the question: how can an organization protect Slack's Primary Owner account with access to such important information?
Securing a Slack-Authenticated Primary Owner
Like many cloud services, Slack has a built-in authentication system. A Primary Owner is set up via Slack's built-in authentication by default. In the past, an organization may have entrusted a system administrator with the Primary Owner's account and password.
This approach causes a single point of failure and limits auditing and accountability. Devolutions Server Privileged Access Management (PAM) is the perfect solution for securing and auditing access to critical accounts.
Traditionally, you might consider PAM most useful for automatically rotating passwords after use. But even with an account that cannot be automatically rotated, such as Slack's built-in authentication, PAM can enhance security by enforcing strong checkout policies.
Configuring Devolutions Server PAM for Highly Privileged Accounts
A key aspect of PAM revolves around checkout policies, and configuring an appropriate policy is easy for an account with high privileges. You can ensure appropriate use and assist auditing by requiring approval and a specified reason for checkout.
- Approval Mode: Mandatory
- Users can approve their own Check-out requests: No
- Include administrators when listing approvers: The recommended setting is No.
- Include PAM managers when listing approvers: The recommended setting is Yes, but it depends on who your PAM managers are.
- Reason Mode: Mandatory
- Check-out Time (minutes): 240 is the default time, but customize it to your needs.
- Ticket Number Mode: Optional but recommended if you have a ticketing system.
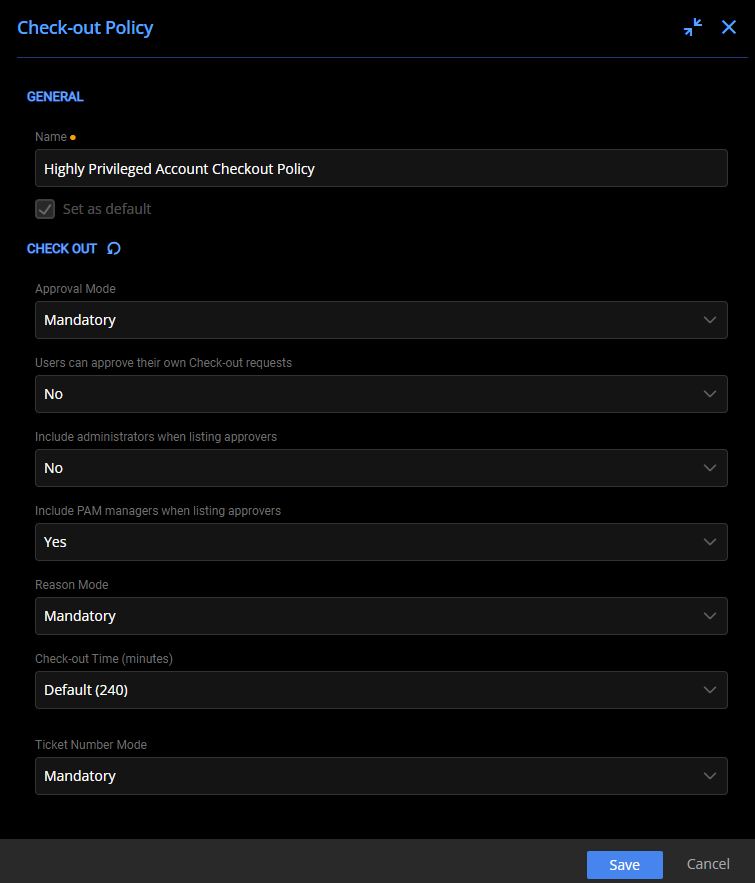
Configuring the Check-out Policy for Highly Privileged Accounts
After defining a custom checkout policy (useful for any privileged account), add the Primary Owner account and assign the newly created checkout policy. Assign custom permissions, if needed, to limit access only to those requiring it. To ensure that this account is well protected, use two-factor authentication with one-time passwords stored in Devolutions Server PAM.
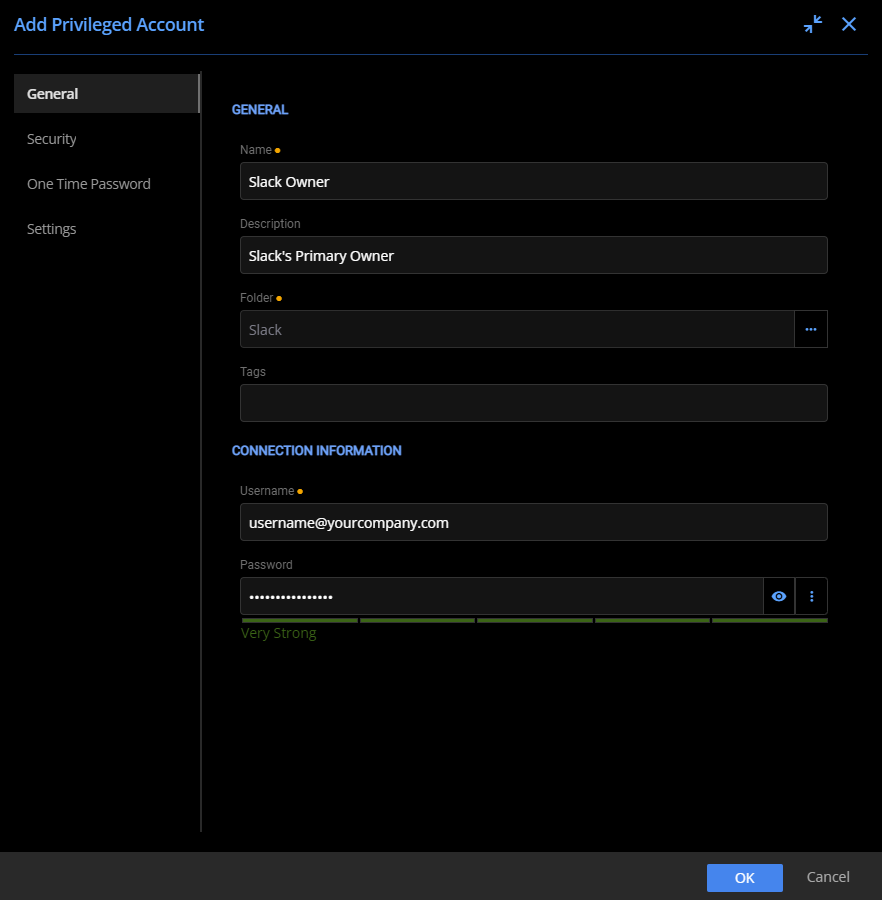
Configuring the General properties of the Standalone Slack account
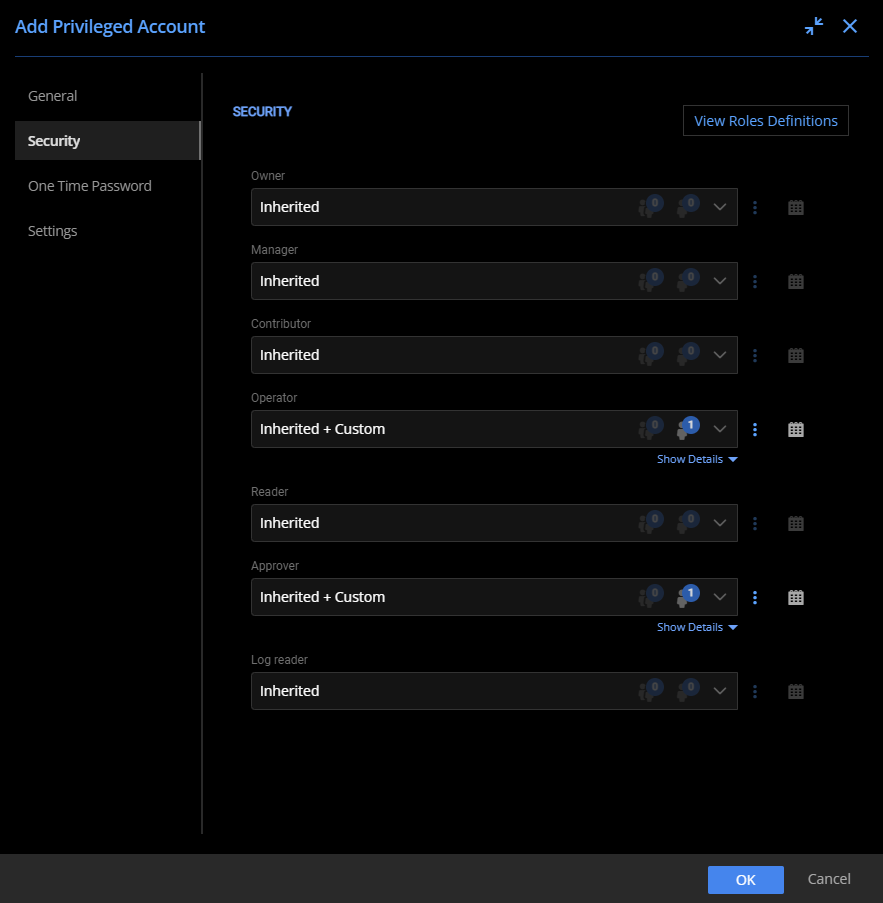
Customizing the Security properties of the Standalone Slack account
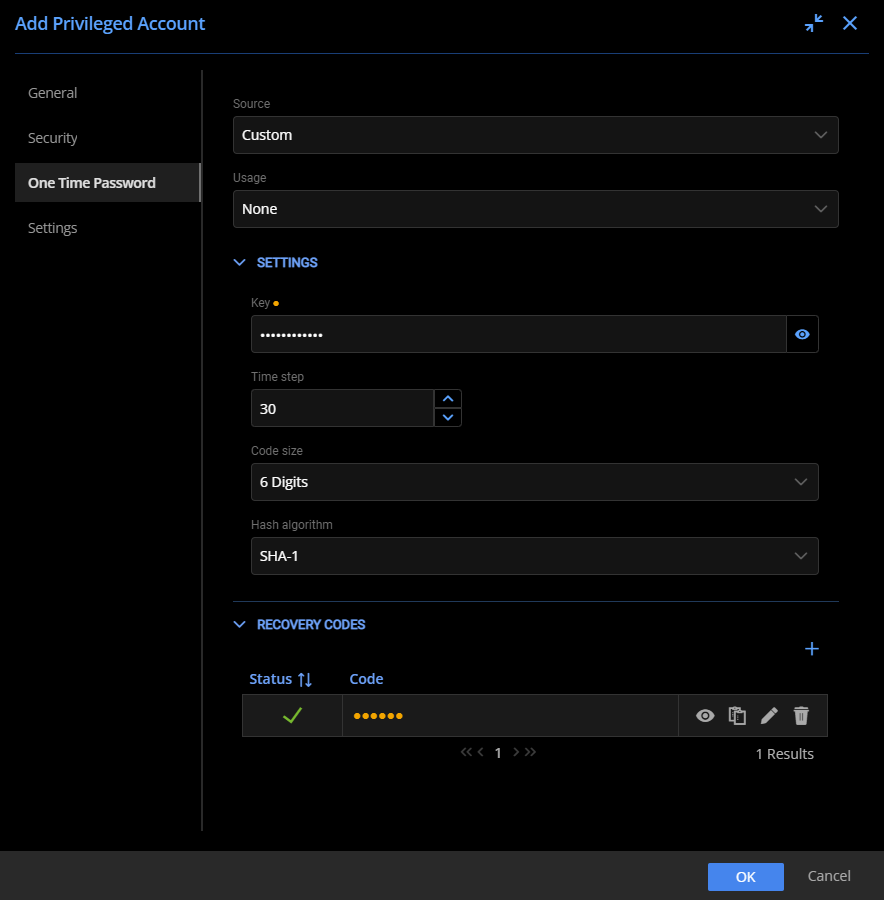
Adding One-Time Password properties to the Standalone Slack account
Configuring a Single Sign-on Primary Owner Slack Account
Consolidating authentication to a central system typically makes management easier. Slack offers Single Sign-on (SSO) integration with Microsoft Azure Active Directory (AD), offering user account management across an organization.
Moreover, a Slack Primary Owner account can be associated with an Azure AD user account. This association unlocks even more powerful Devolutions Server PAM capabilities! With this integration, checking out the Slack Azure AD-integrated account may automatically rotate the password upon check-in. As a result, even if the account was compromised, it would not be accessible for long.
Adding Devolutions Server PAM and SSO to Slack Accounts
In Devolutions Server PAM, an integration with an authentication system is called a Provider. Before configuring the Primary Owner account, create the Microsoft Azure AD Provider interface within PAM. To do so, you need a Tenant ID, Client ID, and Secret Key associated with your Microsoft Azure AD organization.
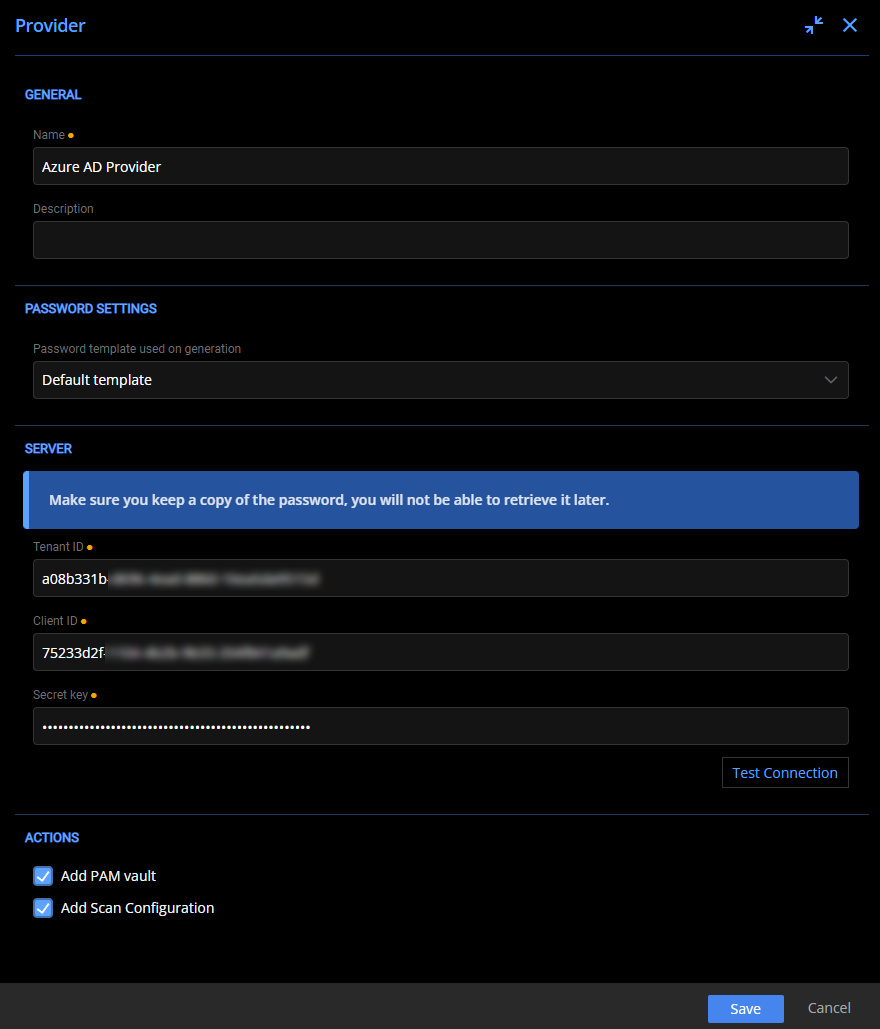
Configuring a Microsoft Azure AD Provider
After configuring the provider, leverage the same checkout policy and create an account linked to the Microsoft Azure AD provider. The main difference is that you may select the option to change the password upon check-in, taking advantage of all that Devolution Server PAM has to offer.
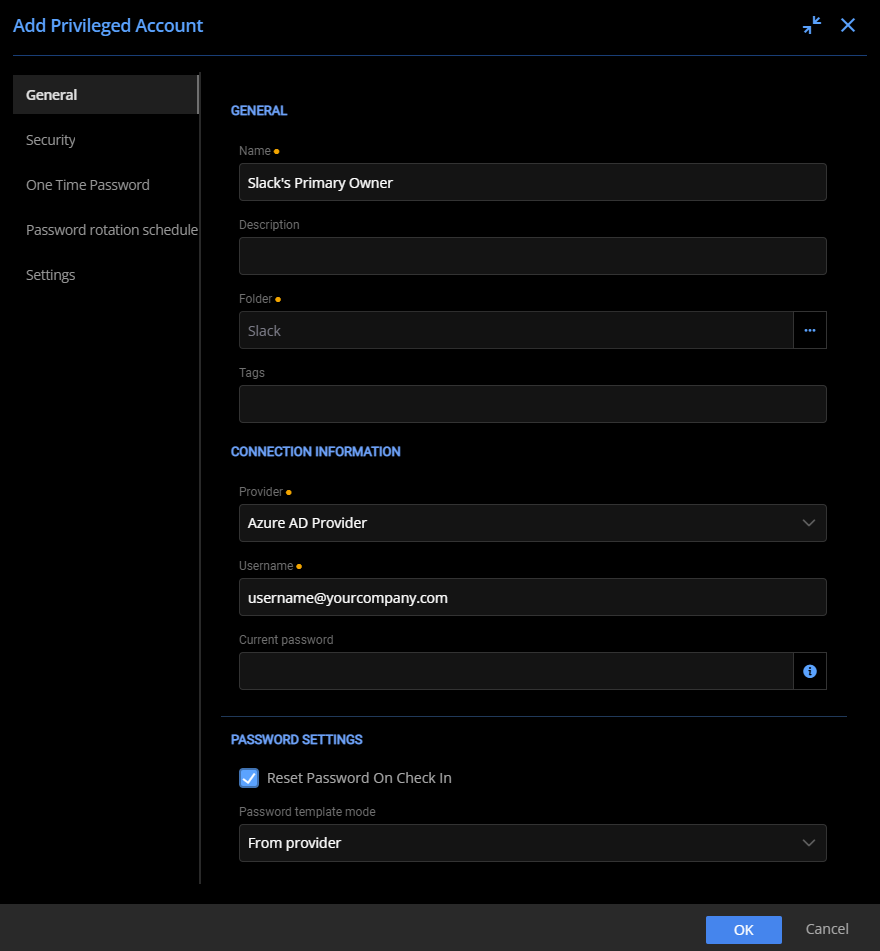
Configuring the General properties of the Microsoft Azure AD integrated Slack account
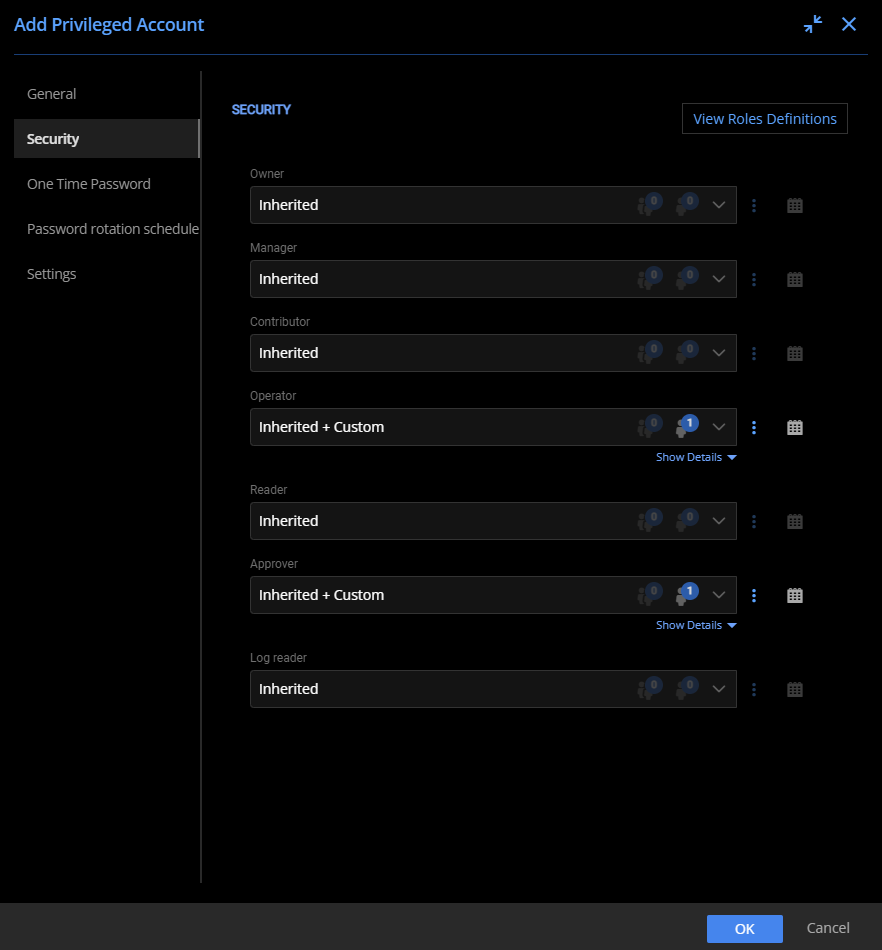
Customizing the Security properties of the Microsoft Azure AD integrated Slack account
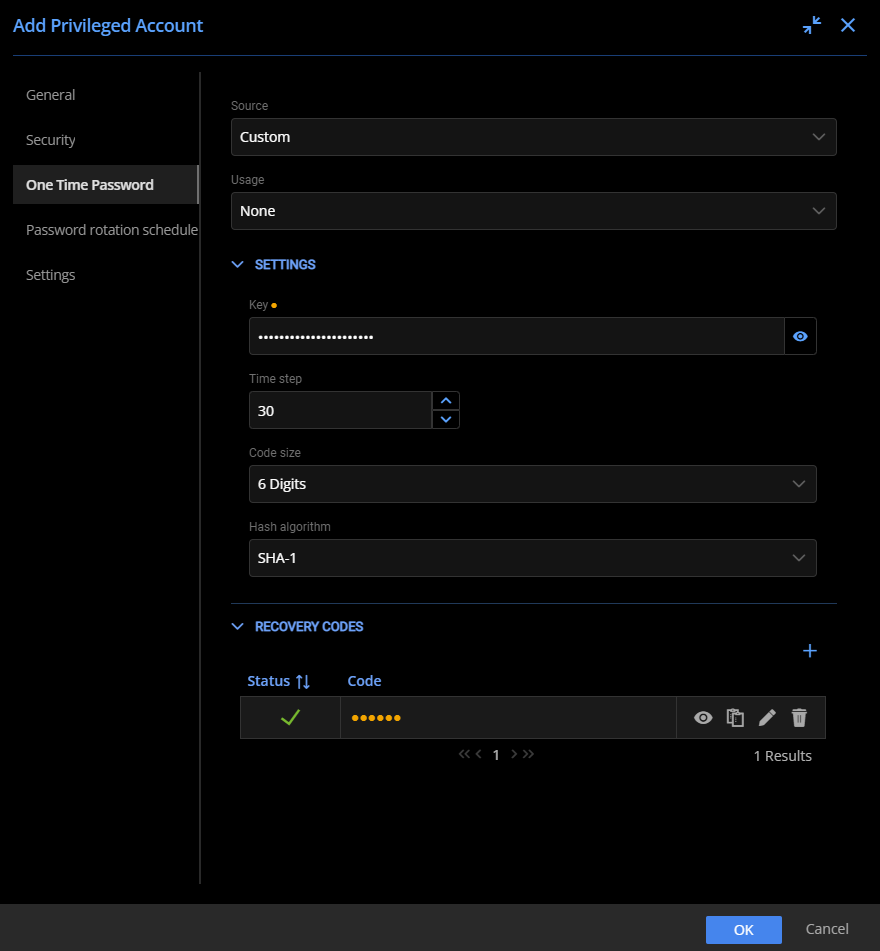
Adding One-Time Password properties to the Microsoft Azure AD integrated Slack account
If Azure AD is unavailable, you may wonder if you can still log in to your Slack account. In this case, instead of selecting the SSO integration as your login method, you would choose the “Sign in with password” option for Slack and use the saved account within Devolution Server PAM.
Auditing Account Usage
All check-outs and password rotations are logged for the Slack Primary Owner, controlled by Devolutions Server PAM. You can navigate to Reports for in-depth auditing information from the following reports:
- Privileged Access - Password Rotation
- Privileged Access - Recent Activities
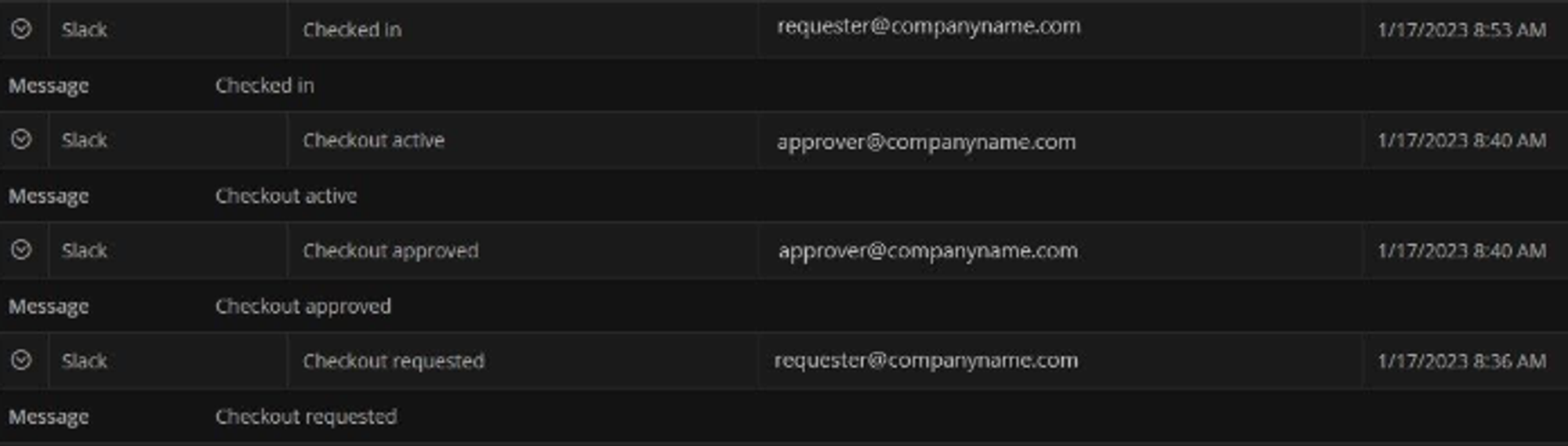
Displaying recent activities for PAM
Protecting Highly Privileged Accounts with Devolutions Server PAM
Increase your organization's security and peace of mind with Devolutions Server PAM. Store your highly privileged accounts within to ensure that only those needing access can access highly privileged accounts, such as the Slack Primary Owner. This protection is backed by extensive logging to monitor who is accessing those accounts and ensure your organization stays safe!





