Hello RDMers!
This is Mathieu Morrissette from the Devolutions Security Team. As you may already know, we have been working on deprecating the security providers in Devolutions Password Server.
Previously, the encryption key was shared with all users. This created some potential vulnerabilities for handling data at rest. Now, when deploying Devolutions Password Server 2019.2.9.0 and above (and when regenerating encryption keys), a new 256-bit encryption key will be generated and stored in the encryption.config file on the server only. This encryption key will be used to encrypt data entries (connections, private vaults, documentation and attachments).
To encrypt the data stored in the database, we use our open-source cryptography library, which can be found at https://github.com/Devolutions/devolutions-crypto. The current version at this time (0.4.0) uses the XChacha20-Poly1305 algorithm.
How to Migrate
First, launch the Devolutions Password Server console and click on the "Manage Security Provider" button.
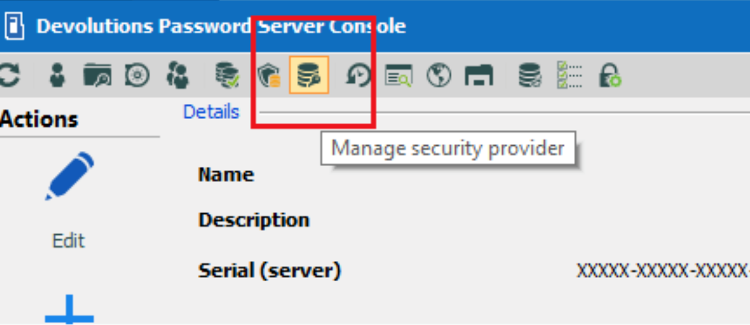

If no security providers are configured, then you’ll see this pop-up which means you don’t need to migrate:
Otherwise, this security provider dialog will open:
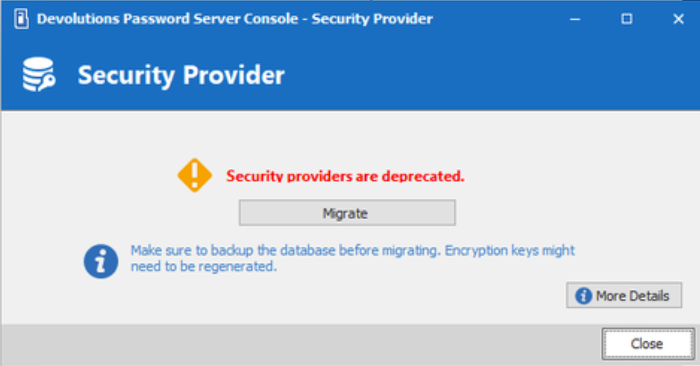
Before migrating, ensure that you back up the database and encryption keys. Then, click Migrate and follow the on-screen instructions. At this point, you might need to regenerate your encryption keys. Once you’ve completed all of the steps, restart the IIS web application (IIS Manager). If you still need to manage security providers, then you can use an old password server console installation.
And there you go! You’re all done, and ready to continue working in a more secure way. We hope that you find this security upgrade beneficial.
As always, please let us know your thoughts by using the comment feature of the blog. You can also visit our forums to get help and submit feature requests, you can find them here.