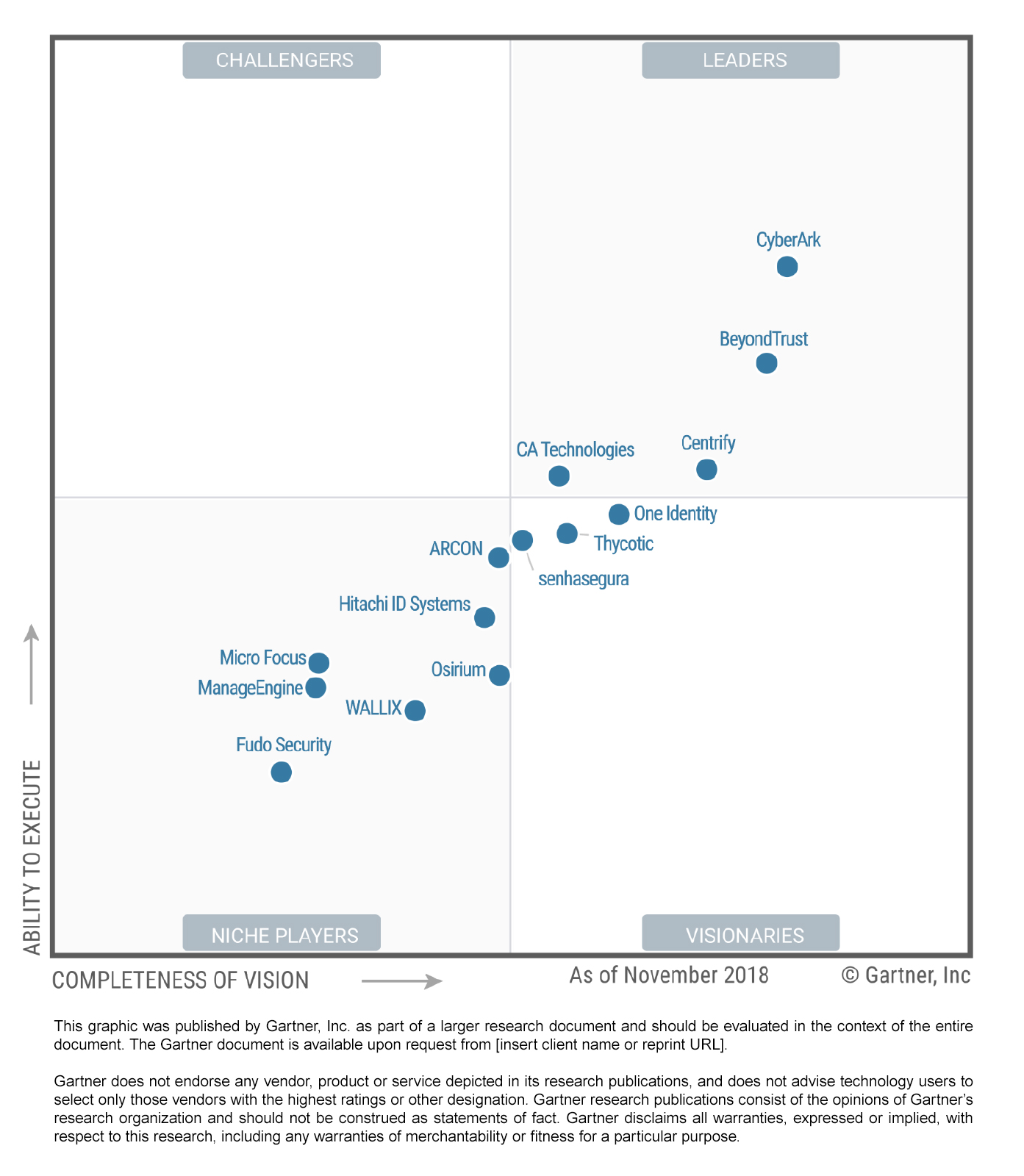
We are pleased to announce that Devolutions has been listed in Gartner’s first-ever 2018 Magic Quadrant for Privileged Access Management.*
Devolutions joins a small group of companies that have been designated as “Honorable Mentions”. These are noteworthy vendors in the global PAM marketplace that, at the present time, do not meet 100% of Gartner’s criteria to be included in the formal Magic Quadrant evaluation process.
Speaking of noteworthy vendors: we would like to applaud four companies in particular that have been listed in Gartner’s Magic Quadrant for Privileged Access Management, and whose solutions integrate with Devolutions Password Server (DPS) and Remote Desktop Manager (RDM): CyberArk, BeyondTrust, Thycotic, and ManageEngine.
CyberArk and Beyond Trust were positioned in the “Leaders” quadrant, Thycotic in the “Visionaries” and ManageEngine were positioned in the “Niche Players” quadrant. Congratulations to each of our integration partners for the well-earned distinction!
PAM Tools & SMBs
Gartner analysts state that “privileged access management is one of the most critical security controls, particularly in today’s increasingly complex IT environment. Security and risk management leaders must use PAM tools in a long-term strategy for comprehensive risk mitigation”.
We completely agree with this view and add that PAM tools are not just essential in large organizations and enterprises. They are also vital in SMBs, which are becoming the ground-zero for cybercrime. Research by the Ponemon Institute found that in 2017:
- 61% of SMBs polled reported a cyberattack — up from 55% in 2016.
- 54% of SMBs reported a data breach, with employee negligence cited as the #1 cause.
- 52% of SMBs reported a ransomware attack — many of which are caused by stolen or compromised credentials.
- The total costs of a successful attack on an SMB now exceeds $1 million.
PAM Is a Long-Term Strategy
The size of the PAM marketplace surpassed $1.1 billion in 2017, which was 16.9% higher than in 2016. The market is expected to continue growing rapidly, with a CAGR of nearly 19% from 2016-2022.***
According to Gartner analysts, factors that are driving this market growth include:
- Organizations that want to reduce the risk of breaches and insider threats, which typically arise from stolen, compromised or misused privileged credentials.
- An increasing number of regulatory and compliance mandates and standards (e.g. SOX, PCI, HIPAA, FFIEC, FISMA, etc.) that relate to controlling privileged users and protecting privileged credentials.
- Organizations responding to auditor recommendations or requirements regarding user management and monitoring, etc.
- The growing need to give third party stakeholders access to provided accounts (e.g. vendors, contractors, suppliers, business partners, etc.).
- The need to enhance the performance, productivity and efficiency of system administrators and operators, and to support an overall security strategy.
PAM Tool Selection
In terms of practical and strategic considerations for PAM tool selection, Gartner analysts advise the following:
- It is important to support a variety of PAM approaches, methodologies and technologies in the environment. A single tool or solution will not get 100% of the job done.
- Seek vendors that are not just targeting today’s PAM capabilities, but are working on innovations for future needs and requirements.
- Understand that going forward, the uptime and reliability of systems must integrate with the availability of PAM access. Improving security and improving productivity must work together and not separately.
- MFA must be required for PAM access, as conventional single-factor authentication is no longer sufficient protection.
- Implementing PAM tools is not just a technology shift, it is also part of a larger organizational change management event.
- The ongoing success and strength of a PAM program depends on program maturity. It is not a “set it and forget it” thing, but an ongoing commitment and evolution.
Market Guide for Privileged Access Management
Last year, Devolutions was listed in Gartner's 2017 Market Guide for Privileged Access Management (PAM).** We joined a small list of select vendors including Red Hat and Microsoft that were designated as effectively delivering an alternative way to mitigate the risks surrounding privileged access, or providing a set of specific and deep capabilities to augment existing PAM deployment. More information is available here.
* Gartner, Magic Quadrant for Privileged Access Management. Analysts: Felix Gaehtgens, Dale Gardner, Justin Taylor, Abhyuday Data, Michael Kelley. 3 December 2018.
** Gartner, Market Guide for Privileged Access Management. Analysts: Felix Gaehtgens, Anmol Singh, Dale Gardner. 22 August 2017.
*** Forecast: Information Security, Worldwide, 2016-2022, 2Q18 Update.
GARTNER is a registered trademark and service mark of Gartner, Inc., and/or its affiliates in the U.S. and internationally, and is used herein with permission. All rights reserved.
Gartner does not endorse any vendor, product or service depicted in its research publications, and does not advise technology users to select only those vendors with the highest ratings or other designations. Gartner research publications consist of the opinions of Gartner’s research organization and should not be construed as statements of fact. Gartner disclaims all warranties, expressed or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose.
Gartner Peer Insights reviews constitute the subjective opinions of individual end-users based on their own experiences, and do not represent the views of Gartner or its affiliates.




