We recently published "Decoding just-in-time (JIT) elevation", an introduction to just-in-time (JIT) privilege elevation and its role in a privileged access management (PAM) strategy. Devolutions PAM offers flexible, just-in-time privilege elevation controls allowing IT professionals to gain positive control over privileged accounts by limiting standing privileges, implementing approval workflows, and automatically rotating passwords after use.
The threat landscape is only getting more complex. The 2024 IBM X-Force Threat Intelligence Index report states that a 71% increase in attacks through valid credentials, year over year, contributes to 32% of data theft and leaks in organizations. Microsoft's 2023 State of Cloud Permissions report illustrates this risk further, finding that over 50% of accessing identities are super-admins using less than 2% of granted permissions.
Introducing Devolutions PAM
How would an organization implement these controls, practically speaking? Beyond JIT elevation, any solution to manage privileged accounts needs several components. To that end, it helps to understand what components Devolutions PAM offers:
- Discover, import, and manage privileged accounts through AnyIdentity providers, PowerShell script-based connectors for virtually any source.
- Request JIT privilege elevation for privileged accounts, with approval workflows, to remove standing privileges and accountability.
- Automatically rotate privileged account passwords after use, limiting the use of stolen credentials.
- Propagate password rotations to down-level systems through the PowerShell script-based propagation engine.
Perhaps the most user-facing control is JIT elevation. Typically, a user will need to access a system or resource, check out a privileged account, and potentially request additional access via JIT elevation.
Practical JIT elevation
How does Devolutions approach JIT elevation in practice? Using Remote Desktop Manager connected to Devolutions Server with the PAM module and linked accounts allows an IT professional to quickly and efficiently use privileged accounts. The video below demonstrates:
- Verifying that connecting to a server without proper JIT elevation privileges fails
- Connecting to a server via RDP using a linked PAM account after JIT elevation
- Verifying that the dynamically created and populated group is removed with RDM's built-in Active Directory dashboard
Simple setup for JIT elevation
Once you have a provider set up in Devolutions Server, you may configure the JIT elevation settings. Recent updates to DVLS added what are known as privilege sets. By defining what sets of privileges are grouped together, you have better control over what groups are assigned to what privileged accounts.
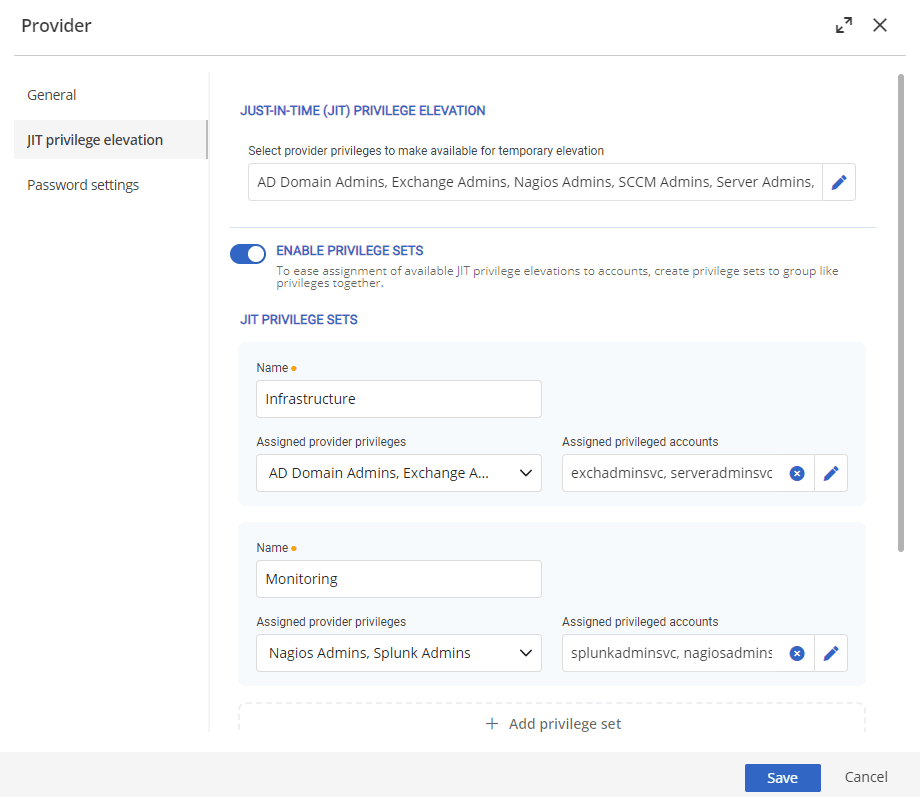
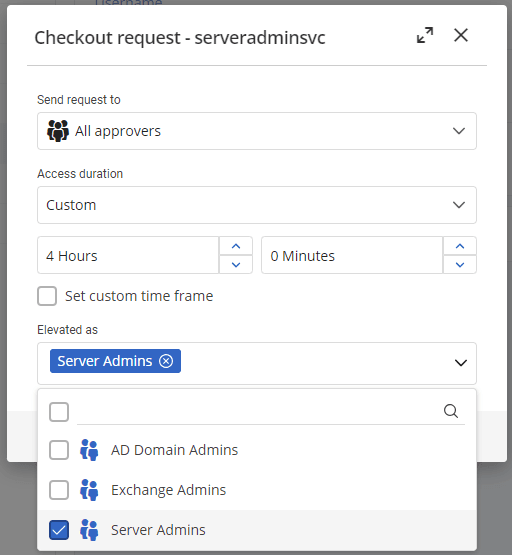
Instead of allowing every elevation group for every account, assign only the relevant groups, protecting accounts from unnecessary temporary privileges. This isn’t limited to one account: request more than one at a time, and, if you’re using an approval workflow, the system will allow the approver to add or remove groups as they deem necessary.
Devolutions PAM is a powerful, flexible, and easy-to-use solution for everyone, from small businesses to enterprise customers looking to protect their privileged accounts. With the Devolutions platform, adhere to the latest compliance standards and keep your IT team efficient and secure!





