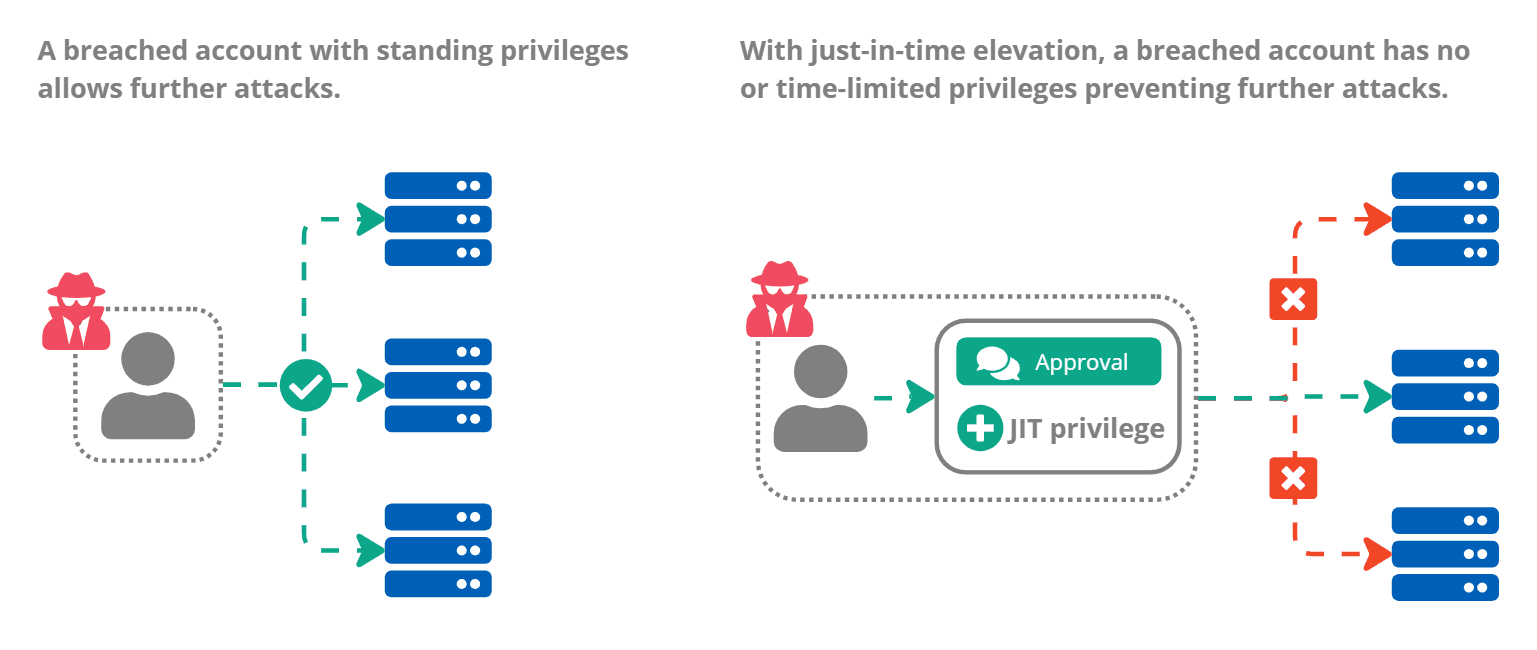
Quickly granted and rarely revoked, privileged access in IT is challenging to manage. Over time, the number of granted privileges accumulates without subsequent removals. When threat actors gain access to an account that has years of accrued permissions (especially true of administrator accounts), they could obtain deep organizational access.
The solution? Grant access only to what users genuinely need and remove access when it's no longer required. Minimize damage caused by compromised accounts by limiting the privileges available. Here, just-in-time (JIT) privilege elevation plays an important role. Keep IT teams efficient by managing account privileges on a time-controlled basis with JIT privilege elevation.
Understanding JIT elevation
The 2024 IBM X-Force Threat Intelligence Index report states that a 71% increase in attacks through valid credentials, year over year, contributes to 32% of data theft and leaks in organizations. Microsoft's 2023 State of Cloud Permissions report illustrates this risk further, finding that over 50% of accessing identities are super-admins using less than 2% of granted permissions.
Just-in-time elevation prevents the accumulation of account privileges. Give users only what privileges they need, when they need them. With the automatic removal of granted privileges, organizations reduce granted privileges to the bare minimum. If, or when, threat actors gain access to your environment, they'll find a limited attack surface to work with, buying you valuable time and protection.
Exploring typical JIT elevation methods
In practice, JIT elevation breaks down into several components:
- Management of what privileges are available for what accounts
- Approval workflows to verify if users should have access
- Methods of granting and removing privileges on a remote system, application, or set of files
Typically, an elevation request occurs within a specific privileged access management (PAM) tool or an elevation dialog in an operating system, like User Account Control (UAC) in Windows. Approval workflows can be built into these requests to ensure a user should be accessing the requested privileges. Though automation in elevating privileges is crucial for maintaining efficiency, adding additional eyes to requests can potentially divert attacks.
Ensuring compliance with JIT privilege elevation
Hand in hand with compliance standards are methods such as JIT privilege elevation, often a component of PAM tools. Developed to ensure organizations and specific industries maintain security in an evolving threat landscape, many regulations mention PAM directly or indirectly.
Removing standing permissions helps to comply with standards and reporting, such as:
All three standards are critical for organizations looking to comply with security best practices, reassure customers and users, and protect themselves against threat actors. Implementing PAM and JIT elevation, in particular, will significantly enhance your organization's security.
With PAM, specifically JIT elevation, allow your users to access what they need when they need it without maintaining unnecessary privileges. Comply with industry standards and maintain efficiency using easy-to-use solutions like Devolutions Privileged Access Management paired with Devolutions Remote Desktop Manager!