As organizations grow increasingly reliant on digital tools and infrastructure, the importance of maintaining robust security controls cannot be overstated. Remote Desktop Manager (RDM) offers various security features, and one of the most powerful tools administrators can leverage to ensure that RDM is used securely is its security dashboard. This blog will explore RDM’s security dashboard in detail — what it consists of, the features it offers, the advantages of using it, and how to effectively navigate it.
What is the RDM security dashboard?
The RDM security dashboard is a centralized interface within Remote Desktop Manager that provides a comprehensive overview of the security status of your RDM environment. It serves as a control center where administrators can identify vulnerabilities, enforce security policies, and ensure that users are following best practices when using RDM. This tool simplifies the process of managing, monitoring, and configuring security settings to address security concerns with ease.
Key features of the RDM security dashboard
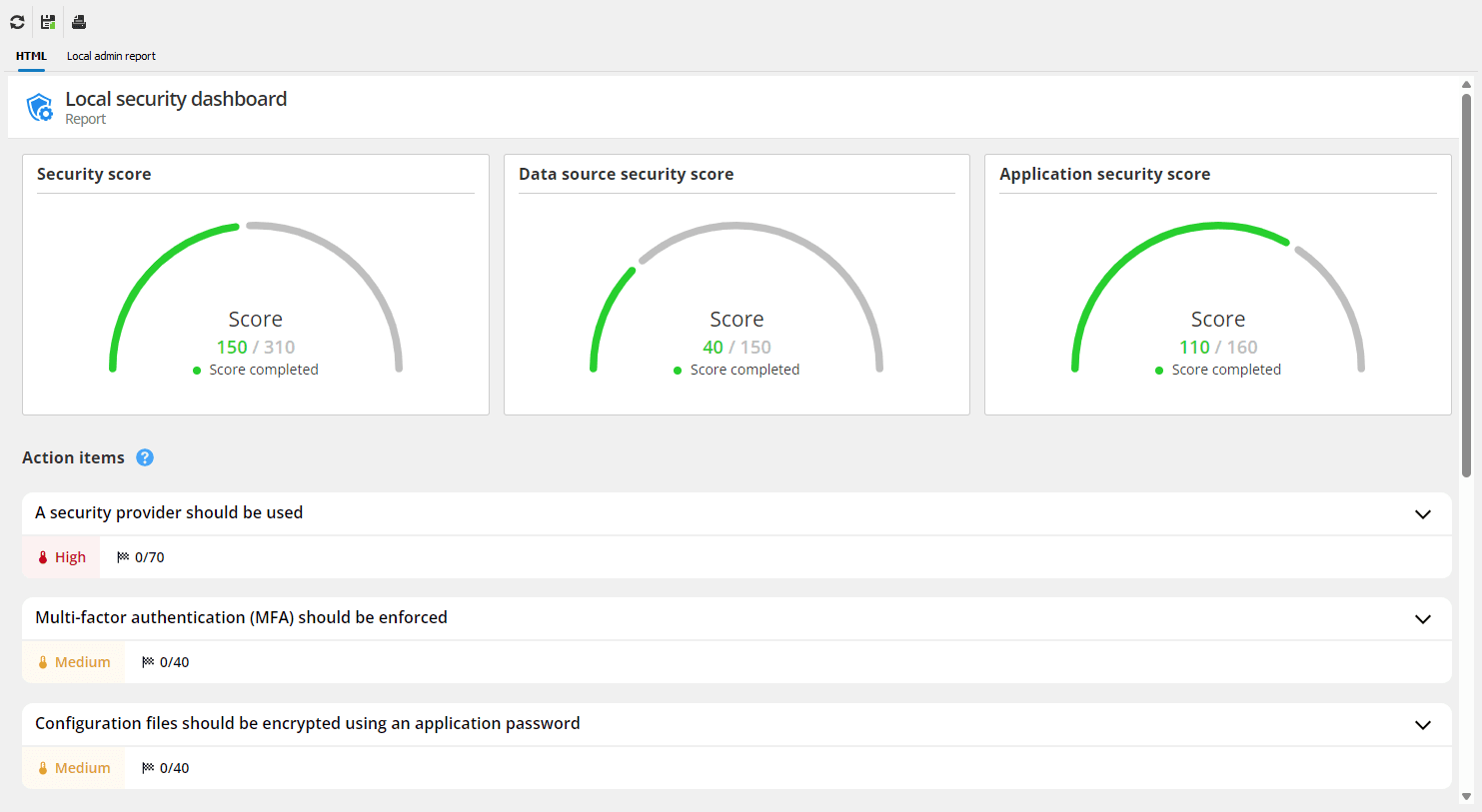
- Security score: The dashboard assigns a security score to your RDM environment based on various factors, such as password policies, user permissions, and access control configurations. This score helps administrators quickly gauge their overall security posture and prioritize areas that need attention.
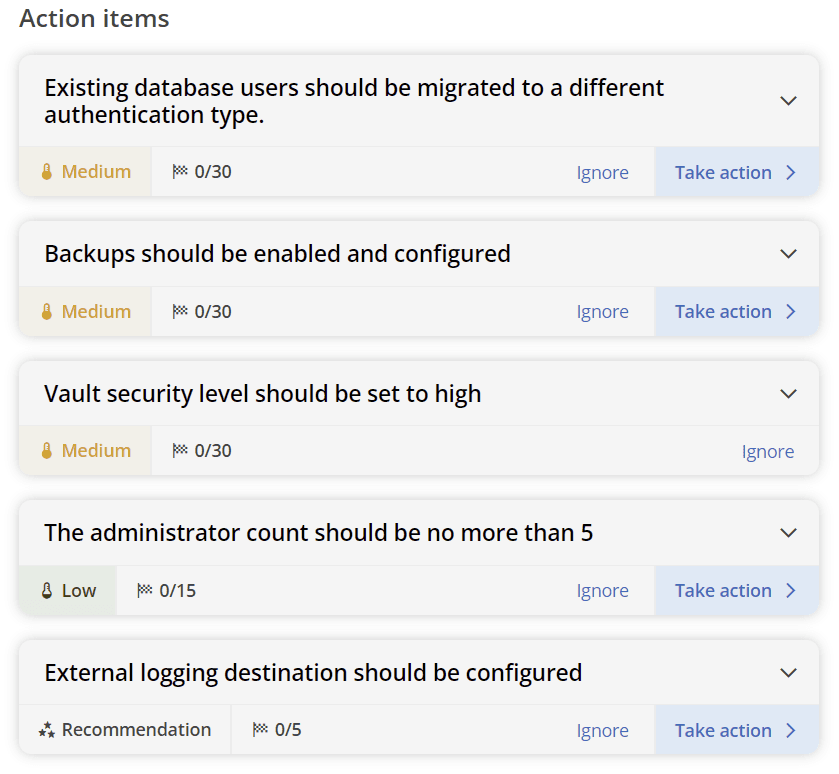
- Security issues list: The security dashboard provides a detailed list of potential security risks, including missing password templates, SSH keys and algorithms that aren’t secure, or accounts without multi-factor authentication (MFA). These issues are ranked by severity, allowing administrators to quickly address the most critical vulnerabilities.
-
Policy enforcement: Administrators can enforce application-wide security policies directly from the dashboard. Whether it’s requiring strong passwords or mandating MFA for all users, the dashboard simplifies the process of ensuring that security policies are consistently applied.
-
Audit and compliance: The RDM security dashboard helps maintain compliance by tracking security settings and changes in real-time. It provides a comprehensive log of security actions, making it easier for administrators to generate reports for internal audits or to meet regulatory requirements.
Advantages of using the RDM security dashboard
-
Comprehensive visibility: The RDM security dashboard provides a bird’s-eye view of the security status across your entire RDM deployment. This centralized control allows administrators to monitor and address vulnerabilities across the board, ensuring no weak link goes unnoticed.
-
Improved security posture: By using the security dashboard to enforce best practices — such as strong password policies, encryption, and MFA — administrators can significantly improve their overall security posture. The dashboard’s security score also serves as a constant reminder of areas that require attention, promoting continuous improvement.
-
Proactive issue resolution: The security issues list helps administrators identify and resolve vulnerabilities before they become significant problems. With customizable alerts and prioritized issue lists, you can stay ahead of potential threats and take action in real time.
-
Streamlined compliance: For organizations with strict regulatory requirements, the security dashboard simplifies the process of maintaining and proving compliance. With detailed actionable items and results, administrators can quickly produce the necessary documentation to satisfy auditors.
-
Time-saving automation: The integration of alerts and simple enforcement of security policies saves time for IT administrators. Rather than having to manually find every security setting, administrators can use the dashboard’s centralized view to manage and monitor security settings efficiently, freeing up precious time to devote to more strategic tasks.
How to use the RDM security dashboard
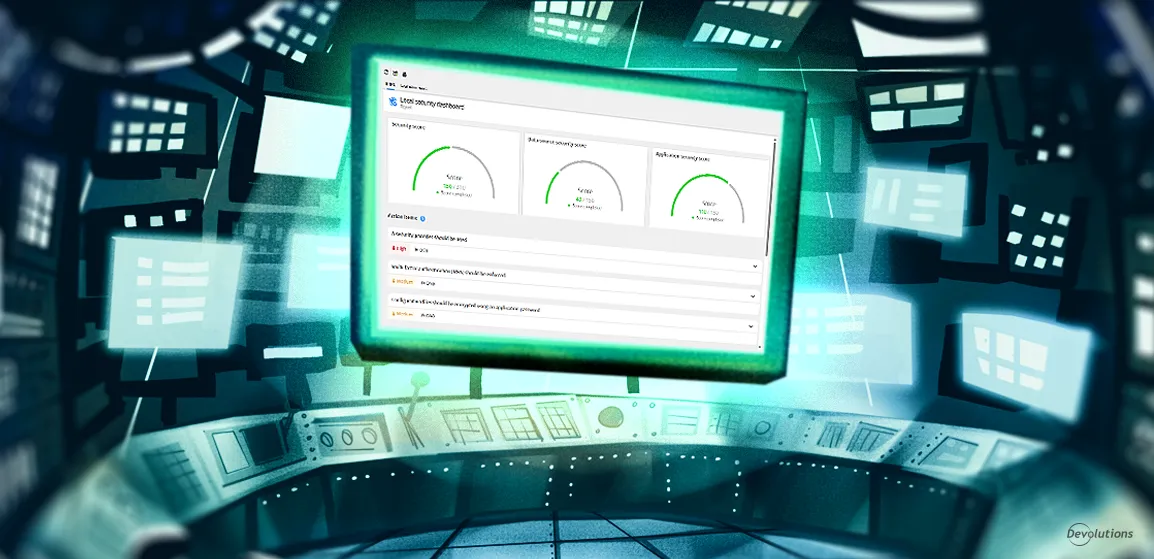
- Access the security dashboard: To begin using the security dashboard, simply navigate to the Reports tab within RDM. Once there, you’ll notice the local and remote security dashboards. The local dashboard is for RDM-related security settings and the remote dashboard is for the data source’s security settings. With these dashboards, you can see the overall security score of your RDM and Devolutions Server environments, which provides a quick snapshot of your current security health. Below is an example of the security dashboard in DVLS (Looking for additional tips for improving security in DVLS? Check out our documentation.)

And here’s an example of the local RDM security dashboard using a SQLite database file.
-
Review security issues: Review the list of identified security risks and vulnerabilities. Since each issue is assigned a severity rating, you can start by addressing the most critical items, such as unencrypted communication channels or accounts without MFA. Selecting any issue provides detailed instructions on how to resolve it.
-
Enforce security policies: From the dashboard, you can configure and enforce security policies for RDM and/or your data source. For example, you can set up a password policy that requires all users to create strong, complex passwords. Policies can also be enforced for MFA, encryption, and user permissions.
-
Audit your environment and generate reports: Use the security dashboard to audit the security configurations of your RDM environment. View which policies are in place, what security issues have been resolved, and which ones still require attention. These items can be useful for compliance audits or for internal review.
Improve your security posture
The RDM security dashboard is an indispensable tool for organizations that prioritize security and compliance. By centralizing security monitoring, automating policy enforcement, and offering real-time insights, the dashboard enables administrators to take control of the application’s security landscape with ease. The detailed security score and issues list provide a clear path for improving the overall security posture of your RDM environment, while customizable alerts and audit logs ensure that no vulnerability goes unchecked.
For more info on using the RDM security dashboard, check out our official documentation.