Staying one step ahead of potential security threats is crucial. AnyIdentity's workflow, built on three key actions - Account discovery, Heartbeat, and Password rotation - forms a robust defense against unauthorized access. Today, we are zooming in on the third and perhaps the most critical step: password rotation.
The culmination of AnyIdentity's workflow
Before we dive into the intricacies of password rotation, let's recap AnyIdentity's four-step workflow:
- Account discovery: Identifies and catalogs privileged accounts.
- Heartbeat: Verifies if stored passwords match current ones.
- Password rotation: Updates passwords when necessary.
- Password propagation: Synchronizes the new password across all connected systems.
Password rotation is the action that ultimately secures your privileged accounts by regularly changing their credentials.
What does the Password rotation action do?
At its core, the password rotation action has one primary objective: to change the password of a privileged account. However, its execution involves several crucial steps:
- Generate a new, secure password.
- Invoke the password rotation action script to update the password on the identity provider.
- Store the new password in PAM.
Like all AnyIdentity actions, the Password rotation action script is written in PowerShell, giving you full control to customize and update as needed.
Password rotation in action
Let's observe a typical scenario to see how Password rotation works in practice. Once a privileged account has been defined to be managed by Devolutions PAM and a manual password reset request, scheduled rotation, or account check-in occurs:
- A new password is generated based on your organization's password policy.
- The action updates the password on the identity provider (e.g., Active Directory).
- The new password is securely stored in PAM.
Here's a simplified version of what a Password rotation script might look like for an Azure Key Vault secret:
$Vault = Get-AzKeyVault -VaultName $KeyVaultName -ErrorAction Stop
$Secret = Get-AzKeyVaultSecret -VaultName $KeyVaultName -Name $Name -ErrorAction Stop
Set-AzKeyVaultSecret -VaultName $Vault.VaultName -Name $Secret.Name -SecretValue $NewPassword -ErrorAction Stop
Configuring Password rotation parameters and action script
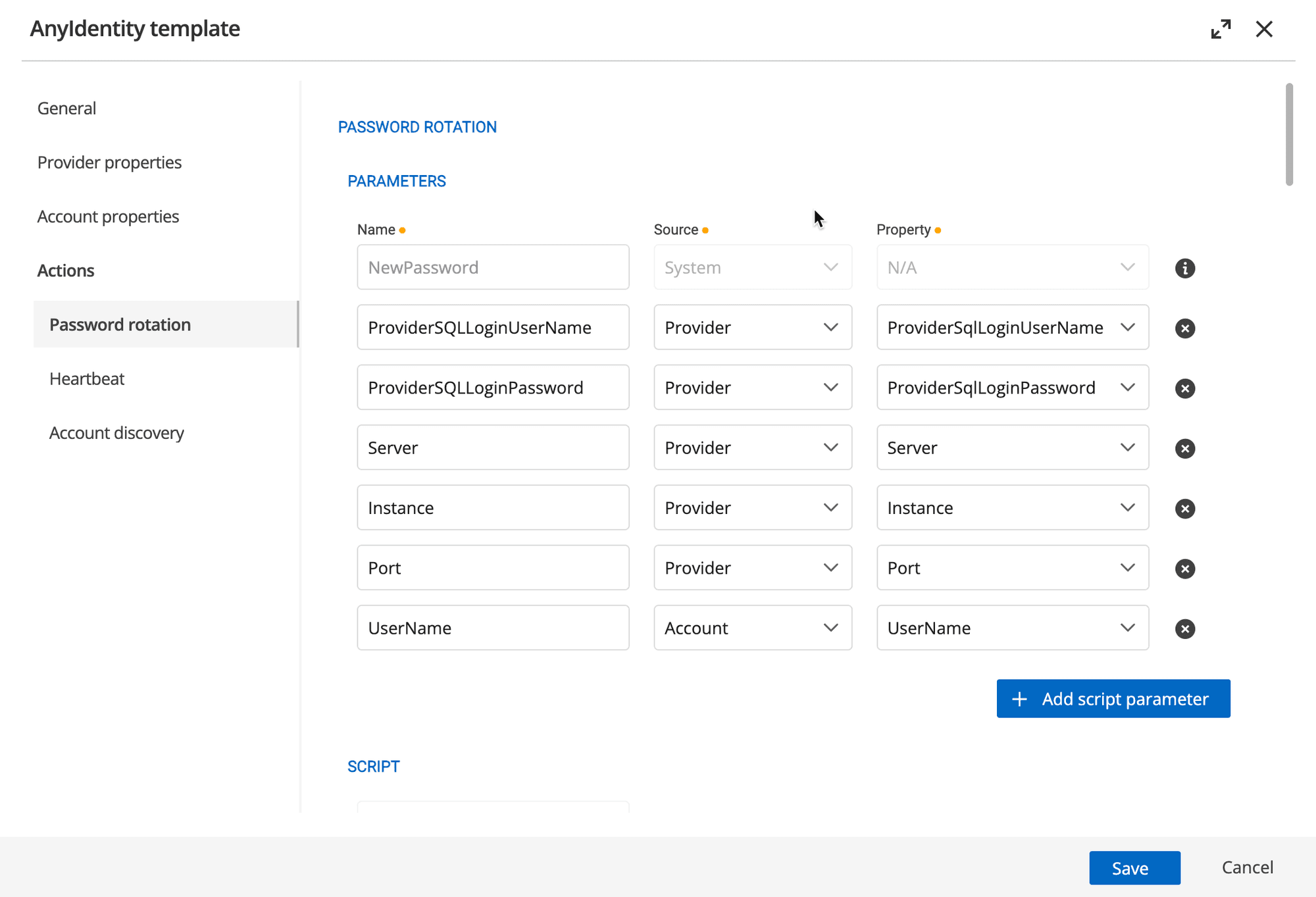
If you’re building your AnyIdentity template, you’ll find script parameters under Actions —> Password rotation.
Script parameters are where you will define any customizable parameters you would like to pass to the Password rotation script.
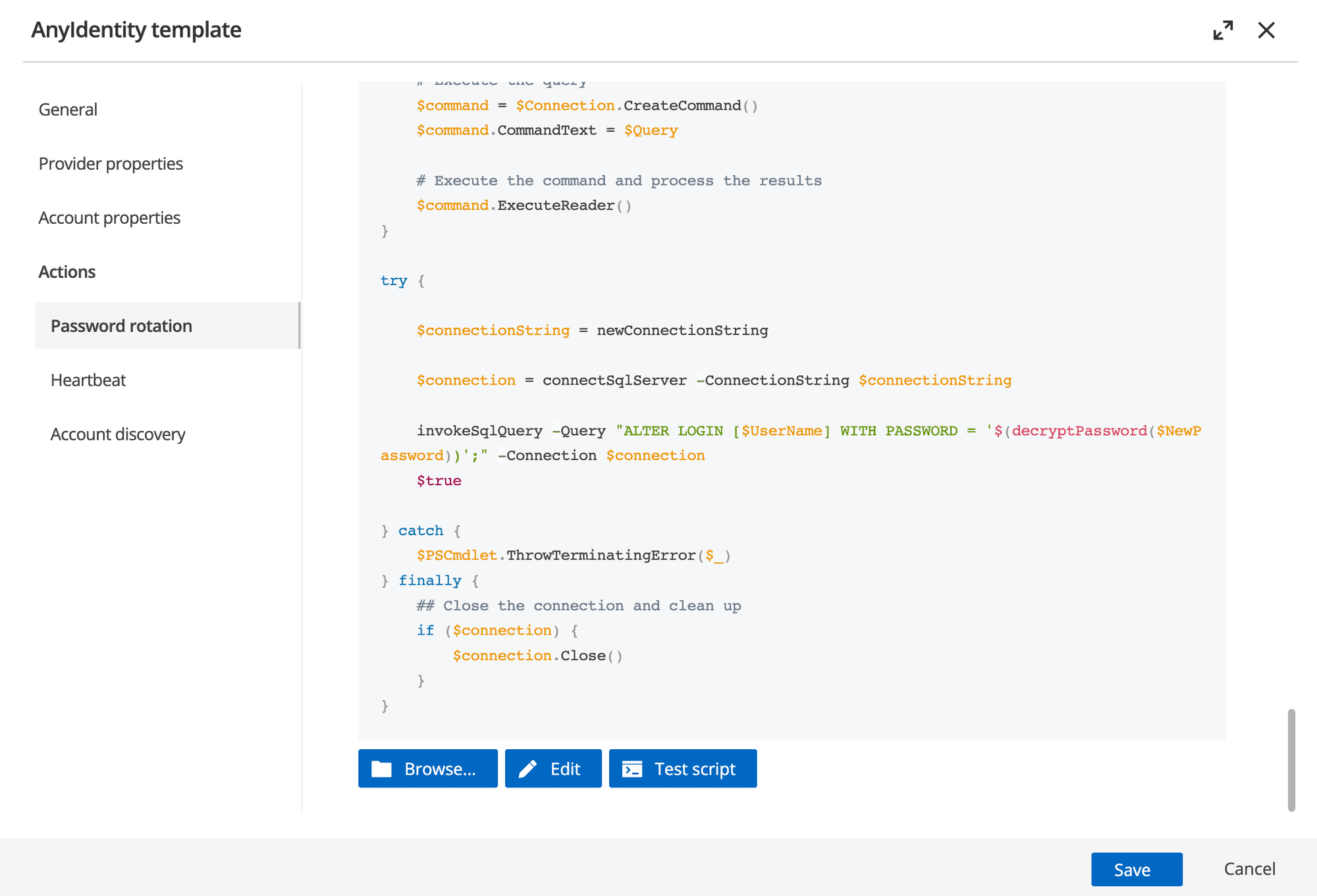
Once the script parameters have been defined, you can add the Password rotation action script.
The actual Password rotation logic is implemented in a PowerShell script, which you can customize to fit your needs.
Note: If you're using a pre-created template from the PAM-Providers repository, you'll simply need to provide values for the mandatory script parameters.
Configuring Password rotation intervals
Once you’ve created the AnyIdentity provider template above and created an AnyIdentity provider from it, you will associate that provider with a PAM vault. The vault allows you to define what users your providers will act on. The vault also allows you to define the Password rotation schedule.
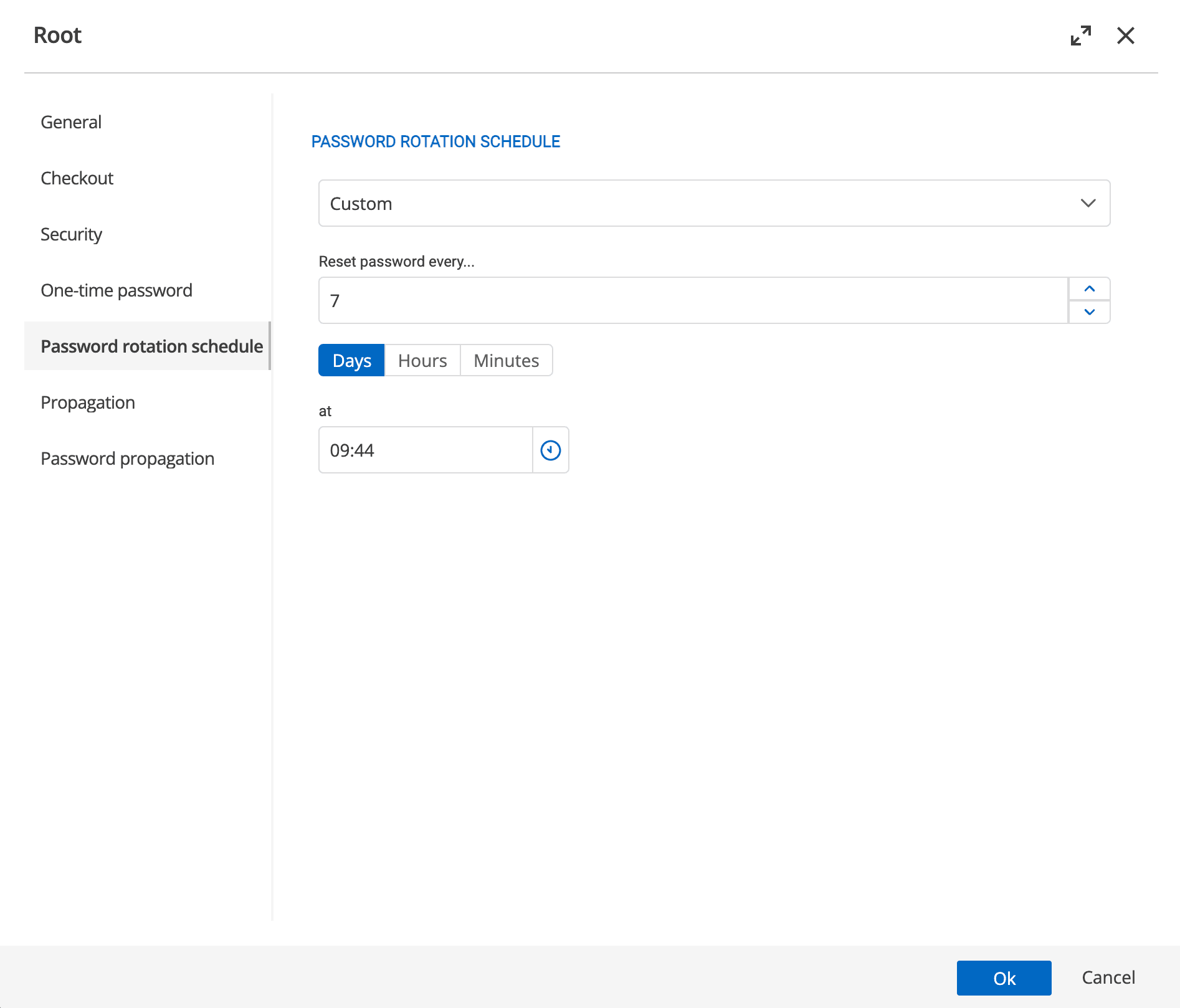
The Password rotation schedule is where you can define how often AnyIdentity changes the password.
Rotating passwords on check-in
If you’re using Devolutions Hub with the PAM module, you have more control and can rotate passwords at check-in, on a schedule, or manually.
Devolutions Hub has you covered if you need more control over when passwords are rotated for your users.
The impact of effective Password rotation
Regular Password rotation significantly enhances your security posture by:
- Limiting the window of opportunity for potential attackers.
- Mitigating the risk of compromised credentials.
- Ensuring compliance with security policies and regulations.
By leveraging AnyIdentity's Password rotation capabilities, you are not just changing passwords – you are actively fortifying your organization's defence against unauthorized access.
Password rotation: The third step in the security cycle
AnyIdentity's four-pronged approach to privileged access management – account discovery, heartbeat, password rotation, and password propagation – forms a comprehensive security strategy. While account discovery uncovers hidden privileged accounts and heartbeat ensures password integrity, password rotation is the final fortress, automatically updating credentials to maintain robust security. These components create a system that continuously adapts to protect your organization's most sensitive access points.
As you implement or refine your AnyIdentity setup, consider how you can optimize the password rotation action to best serve your organization's security needs or create your own AnyIdentity provider with action scripts to start rotating passwords on any identity provider!